Cyber Incident Planning & Response Course
Learn how to implement NIST's Incident Response Lifecycle & ISO 27001:2022 Annex A5.2X
We have trained over 750 organisations including:

.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



NCSC Assured Training In Cyber Incident Planning & Response

|
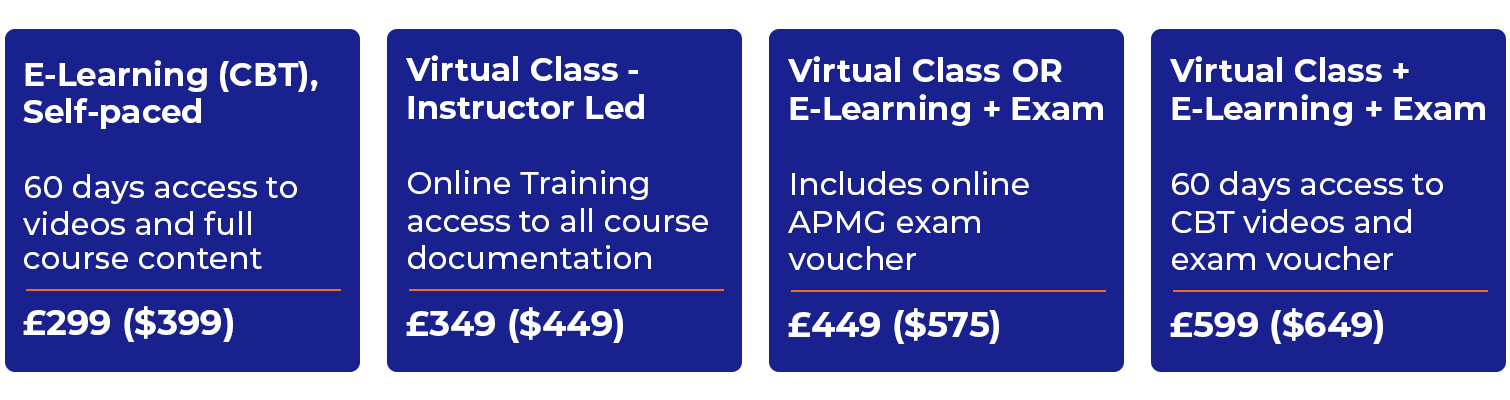
Self-Paced eLearning |
Online Immediate Access |
Click Here |
|
Virtual Live Class |
Thursday 19th June |
Click Here |
Certified cybersecurity training course that teaches you how to:
- Implement NIST's Incident Response Framework
- Meet all the objectives of ISO 27001:2022 Annex A5.2X
- Reduce your time to detect and respond to cyber-attacks
The NCSC Assured Cyber Incident Planning & Response Course (CIPR) created by Cyber Management Alliance, the leading global experts in cybersecurity training and advisory services, is a comprehensive course enabling individuals to prepare a well-defined and managed approach to dealing with a data breach or a cyber-attack.
The course is aimed at a wide audience including those, technical or non-technical, who want to understand how to better prepare for responding to a cyber-attack. The course has no pre-requisites and students will understand the operational strategies and processes an organisation needs to consider before, during and after a cyber crisis or data breach.
Highlights of the Online, Live & Public CIPR Training
Training assured by the UK-Government's National Cyber Security Centre (NCSC)
Teaches how to implement NIST's Computer Security Incident Handling Guide: NIST SP 800-61 Revision 2
Enables meeting the objectives of ISO 27001:2022 Annex A.16.1
Accredited by the Chartered Institute of Information Security (CIISec)
Optional Examination (Provided by APMG International and ProctorU)
19 modules with interactive exercises on key aspects of planning and response
Bonus content including worksheets and templates
Access to several accompanying mind-maps and checklists
Full access to all content (downloadable PDFs) for 60 calendar days (E-Learning students only)
Comprehensive supporting e-book for reinforced learning
Access to regular live-discussions with global experts (online students only)
Exclusive group remote and onsite workshops available
Why do you need the Cyber Incident Planning & Response Training?
Gain a deep understanding of NIST's Computer Security Incident Handling Guide: NIST SP 800-61 Revision 2.
Get insights on the latest techniques and core principles of effective cyber incident response.
Learn how Threat Intelligence-led testing works & what response frameworks are adopted by leading governments & institutions.
Gain mastery over the Cyber Kill Chain and understand how to design an early warning system to lower discovery time from months to days
Attain familiarity with the core concepts of incident triage, OODA and their relevance & importance in a cyber resilient organisation
Become proficient with the primary requirements of privacy regulations, like the EU-GDPR and DORA, in the context of cyber incident response
Personal & Organisational Benefits of the NCSC Assured Incident Response Playbooks Training
There are numerous individual advantages of learning about cyber incident response plans, incident response certifications and knowing how to enhance your incident response capabilities and breach response maturity.
We also run an internal private workshop for organisations who wish to enhance their cyber resilience through improved and a more coordinated response to cyber-attacks. Organisations who invest in the NCSC Assured Cyber Incident Response Training Course for their staff observe a great degree of improvement in their cybersecurity maturity and cyber resilience.
The table below lists the benefits to both individuals and organisations who undergo our NCSC Assured Training.
Individual Benefits |
Organisational Benefits |
| Gain a deep understanding of NIST's Computer Security Incident Handling Guide: NIST SP 800-61 Revision 2. | Learn how to implement NIST's Cyber Incident Response Framework throughout your organisation. |
| Become Certified in Cyber Incident Planning and Response. | Define the threat actors and create a threat actor library specific to your organisation. Define Normal - understand your organisation's baseline. |
| Display your incident response certifications or accreditation via a digital badge, showcase to potential clients and employers. | Assess and improve your organisation's triage capabilities. Define and improve alerts for your analysts. |
| Comprehend and manage the threats and risks relating to information systems and assets from cyber-attacks. | Become more compliant with data breach response regulations by creating fit-for-purpose data breach response plans. |
| Define and support the implementation of processes and procedures for detecting breaches of security policies. | Achieve tangible reductions in detection and response times to cyber-attacks that could lead to better managed and lower data breach compensations. |
| Understand the core principles of and actively contribute to the creation of your organisation’s cybersecurity strategy and incident response plans. | Streamline technology investments with the possibility of tangible savings across multiple technology sets. |
| Explain what Threat Intelligence and its significance is in keeping organisations cyber-resilient. Discuss how Threat Intel can aid in rapid detection of advanced threats. | Create organisation specific cyber-attack scenarios. |
| Participate in the development of information risk management strategies to reduce business risk. | Build Detection & Response Strategies tailored to your business. |
| Discuss the benefits of monitoring and auditing for violations of relevant security policies (e.g. acceptable use, security, etc.). | Technology stack review & assessment of integration into SoC & monitoring technologies. High level review of your monitoring and log management. |
| Define and implement processes and procedures for detecting data breaches. | Improve interdepartmental communication and interaction before and during an incident (This is especially true when organisations host the CIPR workshop internally, over 2 days). |
| Establish and maintain a Computer Security Emergency Response Team to deal with breaches of security policies. | Review your PR & communication templates & internal communications approach. |
| Understand and explain the primary requirement of privacy regulations, like the EU-GDPR, in the context of cyber incident response and cyber resilience. | Review and improve the team and organisational structure of IR teams and CSIM (cybersecurity incident management) teams. |
| Discuss and support the development of innovative methods of protecting information assets, to the benefit of the organisation and the interface between business and information security. | Understand areas of improvement of your organisation’s incident response plans. Baselines cyber resilience awareness across the business. |
| Discuss and support in the development, coordination and evaluation of plans to communicate with internal stakeholders, external stakeholders and the media. | Achieve more productive and efficient staff with increased motivation and better learning and career development. |
Continuing Professional Development
- CPD points can be claimed for this course at the rate of 1 point per hour of training for this NCSC Assured and CIISec-approved course (8 points for one-day public course and 15 points for the two-day internal workshop).
- (ISC)2 members can claim 8 CPE points after they complete the whole course and obtain the attendance certification.
- ISACA members can claim 8 CPE points after they complete the whole course and obtain the attendance certification.
Learning Objectives
Here's a quick look at what delegates can look forward to learning in our NCSC Assured Training in Cyber Incident Planning and Response.
For a more detailed view of the Learning Objectives, you can directly download Complete Learning Objectives PDF.
Cyber Incident Planning & Response Training
Our NCSC Assured Training in CIPR has been created by one of the world's leading cybersecurity practitioners & a practising global CISO. The CIPR course stands apart for:
- It's interactive and engaging approach to Cyber Incident Response.
- The exceptional course content that is enriched with real-world examples and applicability.
- The compelling bonus materials that ensure continuous learning for attendees even after the training is over.
- Providing learners with best practices, operational and tactical strategies, and practical steps to develop a defined and managed approach to cyber incident response.
Course Content
All the content you need to implement NIST's Computer Security Incident Response Handbook.
All online and public students receive numerous takeaways including immediately usable cyber response checklists, templates like cyber response plans and workflows that you can put to use in your organisation immediately.
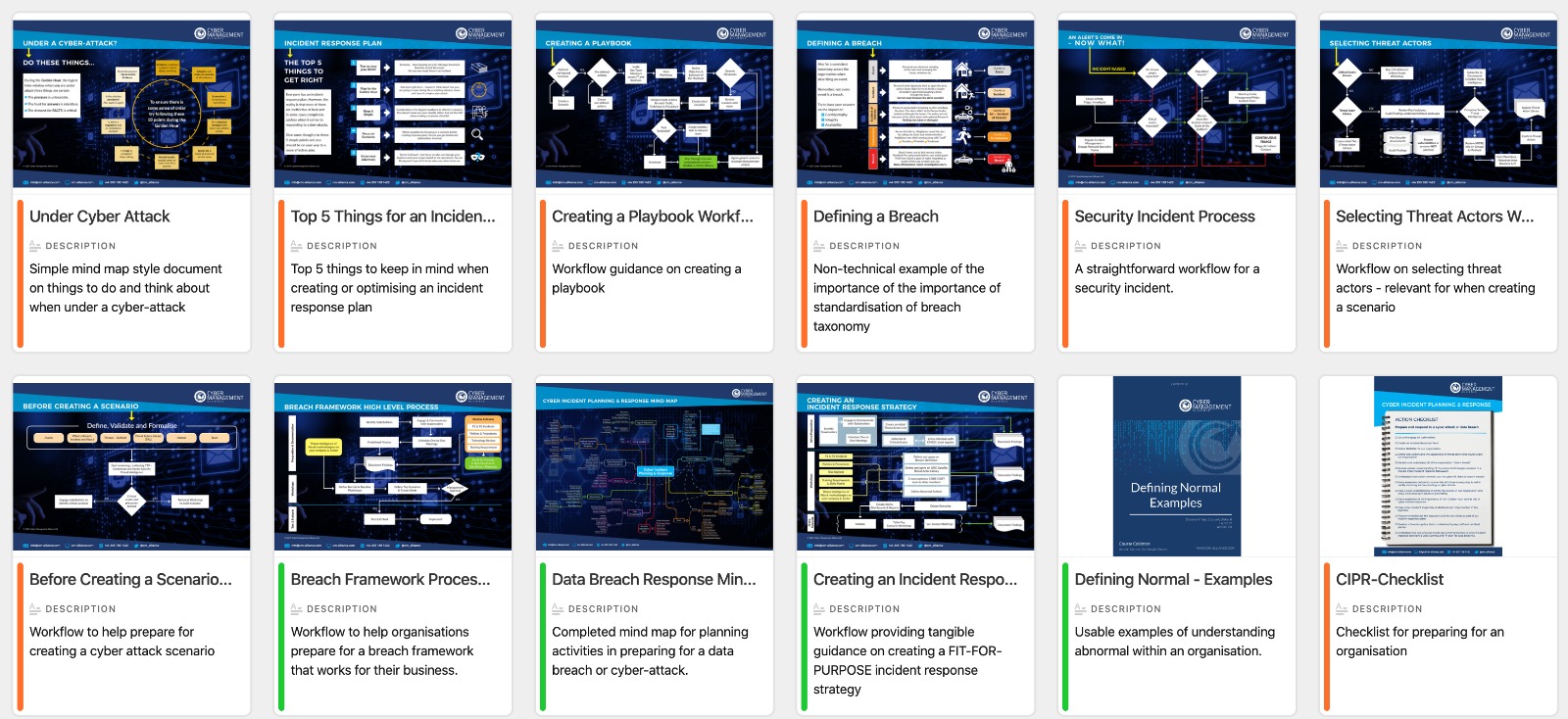
Cyber Incident Planning & Response Course Modules
-
Interactive Exercises and Collateral
- Mind Map: Comprehensive exercise on planning for a Cyber-attack
- Process Workflows: Creating an Incident Response Strategy
- Process Workflows: Selecting Threat Actors
- Process Workflows: Creating a Breach Readiness Framework
- Process Workflows: Responding to an Incident
- Defending against the Cyber Kill Chain
- Visibility: Identifying your Crown Jewels
- Visibility: Identifying Critical Log Data
- Client and PR Communication Templates
- Worksheet: Identifying Privileged Threat Actors
- Worksheet: Defining & Base-lining 'Normal'
-
Module 1 - Cyber Resiliency
This module starts by emphasising the importance of asking the question - WHY? Why would an attacker attack your organisation? It delves briefly into the psychology of attacks and builds the foundation for Module 2. In addition, this module introduces the core concept of resiliency in the context of cyber. The module offers:
- A mind-map that will help you answer this question and also understand what the attacker intends to do with your crown jewels.
- Explanation of the “whys” with relevant real-world examples.
- A definition of the ‘Security Fallacy’ and how to work around it.
- An understanding into why merely denying entry to criminals isn’t enough.
For full details on this and other modules click here.
-
Module 2 & 2a - Understanding Threat Actors
Threat actors may sound daunting but fear not. After asking the question, “Why” in the first module, this cyber threat actor section discusses the importance of asking - WHO could damage your critical assets and consequently destroy your business. This section explains the importance of knowing details about your attacker(s) who could target your business. This module offers:
- An introduction to threat actors, intent and attributes.
- Threat actors in detail.
- The TAL or threat actor library and its purpose.
- Building the Threat Actor Profile.
For full details on this and other modules click here.
-
Module 3 - Define Normal
Another key concept in the Cyber Incident Planning & Response course, Define Normal introduces the important idea of baselining or defining an organisational normal and explains its importance in building a cyber resilient business. It goes without saying, unless you can define and understand what’s normal for your digital network, it will be almost impossible to rapidly detect the abnormal. In this module, you will learn:
- The importance and relevance of this concept, with examples.
- How to define ‘normal’ for your organisation based on the nature of your business, scale, operational model etc.
- Applying 'Define Normal' in an organisational context.
- Understanding and building the organisational baseline.
For full details on this and other modules click here.
-
Module 4 a,b,c & d - The Cyber Kill Chain
Cyber criminals follow a process and have their own easy-to-follow attack methodology. In this module (also known as the cyber-attack process), we disclose the specific workflows that the majority of advanced and/or smart criminals utilise when they attack organisations and nation-states.
In these four modules, you will learn:
- The different phases of attack methodologies.
- Analysis of the Cyber Kill Chain (copyright Lock Heed Martin).
- The importance of knowing the process flows that can help in the understanding of specific threat models and methodologies.
- Strategies to counter the Cyber Kill Chain.
For full details on this and other modules click here.
- The different phases of attack methodologies.
-
Module 5 - Visibility
In this module, we introduce an important strategy - the concept that every business must focus on if it wants to increase its breach response and preparedness. The notion that if you stand in a dark room you are blind and oblivious to the surroundings may seem obvious, but this very fact is ignored and overlooked by organisations when planning and strategising on breach-readiness. In this module, students learn:
- What is visibility and why it's so important as a strategic item in a cyber resiliency strategy.
- They key and core concepts and terminology to better understand its overall impact on resilience.
- The importance of log data and its relationship and importance to cyber resilience.
- The primary requirements for increasing visibility in an organisation.
For full details on this and other modules click here.
-
Module 6 a, b, c & d - The Golden Hour & Incident Management
The pivotal moment, the ‘golden hour’ and many other important concepts and strategies are discussed in this section.
- Module 6a deep dives into the ‘golden hour’, its relevance in incident response and its overall importance in the whole incident management lifecycle. This particular module goes deeper into the important aspects of the golden hour, discusses the importance of taxonomy and communications along with introducing and explaining the critical phase of triage and its role in incident response.
- Module 6b & 6c discuss standards and workflows on incident management introducing several different terms and approaches on optimising existing processes and procedures while maintaining alignment with the various standards and touch on the key benefits of incident response playbooks.
- Module 6d takes the student through an exhaustive thought process on creating an effective and fit-for-purpose incident response plan with a comprehensive exercise utilising a mind-map based approach.
For full details on this and other modules click here.
-
Module 7 - Building the Team
Building a great cybersecurity team also involves walking the tightrope between having a great internal team and liaising with external experts wherever necessary. In this module on Building the Team, students will learn:
- Identifying the stakeholders, the 'who' and 'what functions' should be included in the core cyber incident management team.
- Key skills and traits that are essential in members of an effective cyber incident response team.
- Why contextual experience is more important than technical knowledge when building an incident response team.
- The importance of encouraging a culture of speaking up in the team, regardless of seniority or experience.
For full details on this and other modules click here.
-
Module 8 - Forensics & Investigations
Forensics and evidence are often overlooked in cyber incident management. Many IT professionals don't have enough experience in handling evidence the right way. Dealing with a cyber-attack requires the ability to ensure chain of custody and ensure the evidence is captured, protected and processed in a way that it can be presented in court without anyone being able to challenge the integrity of that evidence. Delving further into this subject, in this module, we cover:
- Introduction to forensics principles.
- Why organisations must sensitise their employees about the regulatory requirement to protect evidence and ensure its forensic integrity.
- What is a forensics policy, how it can be created and what should its key constituents be?
For the full details on this and other modules click here.
-
Module 9 - Regulations & Standards
The actions that an organisation takes before, during and after an incident can have legal and or financial repercussions. It is imperative, therefore, that the management, IT and Security teams understand the regulations and standards that apply to them and have a well-defined set of policies to cover these regulations. In this module, we cover:
- The legal, financial or reputational impact that a business can suffer on account of incorrect actions.
- A look at some common regulations and standards that businesses should be aware of.
- What is a breach notification and how is it defined in the GDPR?
- The fines that GDPR stipulates on businesses that are in breach of its regulations.
For full details on this and other modules click here.
-
Module 10 - The Technology Stack
It goes without saying that technology plays an extremely crucial role in all aspects of cyber incident response and management. The challenge is that most organisations have a messy and complex technology stack. A huge part of the objective of cyber incident planning and response is to evaluate your technology stack and ensure that it is optimised and ready for a cyber-attack. In this module, students will learn:
- The common mistakes organisations make while buying technology and building a technology stack.
- The problems a disorganised and incoherent technology stack can create for the business in case of an incident.
- Understanding the technologies that underpin an effective breach-ready organisation.
- Analysis of core technology requirements.
For full details on this and other modules click here.
Cyber Incident Response Course - Testimonials

A really good session. The trainer is really knowledgeable and presented the course in a really understandable format that the participants really enjoyed.

It was really spot on, very practical, non-technical. I have a couple of great take aways for my every day work. Highly recommend it for non-technical people.

It was amazing. Amar is not just a trainer, he’s an industry expert, and from his experience and knowledge, I actually got some amazing insights.

I found today’s course very productive - discussing the various aspects of incident response. The course is very clearly presented; I fully understood the content and look forward to putting some of the stuff into practice. Thank you.

Brilliant course with lots of good examples. A course to recommend to any incident response team.

I feel the day was really well spent in terms of understanding and getting newer or additional knowledge around this concept and the trainer was absolutely wonderful in sharing and articulating this.

I have been attending CMA’s Cyber workshop and we’ve been reviewing incident response. They’ve been directing us towards good cybersecurity practices; they’ve been reviewing our current ideas, and they’ve been adding real value to our Cyber Security response. I thoroughly recommend using CMA for the future.

I have attended the CIPR training course and I have to say I was very impressed with the course and its content. You don’t need to have IT skills or an insight into IT. But what it does do is, in layman terms, sets out the key issues. This course is very good.

I wish all Senior Executives attend this course. It’s the most practical course I have ever attended. It teaches you not just how to understand but also how to respond to a Cyber Attack.

I found the course to be very interesting. It's not the usual bookish theoretical type of course. It was quite interactive.
About the NCSC - National Cyber Security Centre
 Launched in October 2016, the NCSC or National Cyber Security Centre is headquartered in London and brings together expertise from CESG (the information assurance arm of GCHQ), the Centre for Cyber Assessment, CERT-UK, and the Centre for Protection of National Infrastructure.
Launched in October 2016, the NCSC or National Cyber Security Centre is headquartered in London and brings together expertise from CESG (the information assurance arm of GCHQ), the Centre for Cyber Assessment, CERT-UK, and the Centre for Protection of National Infrastructure.
The NCSC Assured training is designed to assure high-quality training courses delivered by experienced training providers. The courses are assessed at two levels, namely, awareness and application.
 This course has been certified for the application level of incident response in the areas of Risk Assessment, Business Continuity Planning and Incident Management. The Application level is for anyone looking for in-depth courses for their professional development.
This course has been certified for the application level of incident response in the areas of Risk Assessment, Business Continuity Planning and Incident Management. The Application level is for anyone looking for in-depth courses for their professional development.

The Chartered Institute of Information Security (CIISec) is the only pure-play information security institution to have been granted Royal Charter status and is dedicated to raising the standard of professionalism in information security. CIISec represents professionalism, integrity and excellence within the information and cybersecurity sector.
The NCSC Assured Training and the Chartered Institute of Information Security's (CIISec) accreditation enables organisations to distinguish between reputable courses and ones that have not been validated using a Government-endorsed assessment process.
Optional Online Examination
Following the completion of the training course (Public, Internal, Instructor-led or Self Paced Learning) all students have the option of earning incident response certifications by successfully passing the APMG International examination of the NCSC Assured Cyber Incident Planning and Response Training. The exam is administered by APMG International and invigilated by ProctorU who provide secure live and automated online proctoring services for academic institutions and professional organisations.
Number of Questions: 30
Passing Score: 50%
Exam Duration: 25 Mins
Exam Format: Multiple Choice
Exam Delivery: APMG Exam Portal and ProctorU
 Our digital badges are issued by youracclaim.com, the world's most trusted digital credential network for professional associations and corporate learning. The badges are secure, digital representations of your professional development credentials (certification in incident response). Embed your digital badge on an email signature, website, social media profile or a digital CV.
Our digital badges are issued by youracclaim.com, the world's most trusted digital credential network for professional associations and corporate learning. The badges are secure, digital representations of your professional development credentials (certification in incident response). Embed your digital badge on an email signature, website, social media profile or a digital CV.
With just one click, employers, clients, customers and other interested parties can easily view and verify your credentials and skills.
Students who have passed the exams and earned certifications in incident response have come from organisations including Microsoft, Adobe, NHS, numerous Government departments and Police forces, Unilever, IBM, CISCO, Ernst and Young, Deloitte, KPMG, UBS, RBS, Barclays, Goldman Sachs, Bank of America, TATA Consultancy Services and many many more.
Meet the Trainer
Amar Singh has a long history and experience in data privacy and information security. Amar has served as CISO for various companies, including News International (now News UK), SABMiller, Gala Coral, Euromoney and Elsevier. Amongst various other activities, Amar is a Global Chief Information Security Officer and Trusted Advisor to a number of organisations including a FTSE100 firm, and is chair of the ISACA UK Security Advisory Group. He also founded the not-for-profit cybersecurity service for charities, Give01Day.
.jpg?width=720&height=163&name=Amar_Singh_CISO%20(1).jpg)
Amar has the highest integrity and is trusted by FTSE100 companies with some of the most sensitive commercial information. He has been involved with highly sensitive forensic investigations.
He has the ability to deal with both technically-astute, board-level executives and lead an organisation's information security direction. Apart from his experience and abilities, Amar holds a number of industry-recognised certifications, such as ISO 27001 Certified ISMS Lead Implementer, MoR, CRISC and CISSP certification.
Amar is an industry-acknowledged expert and public speaker and is regularly invited to speak and share his insights by some of the largest and most respected organisations in the world including The BBC, The Economist’s Intelligence Unit, The Financial Times, SC Magazine, InfoSec Magazine, Computer Weekly, The Register and the AlJazeera English Channel.

Why not book a discovery call to discuss your requirements?
Want more information on the NCSC Assured Training in Cyber Incident Planning and Response? Book a no-obligation discovery call with one of our consultants.
The information on this page and related pages and documents is Copyright of Cyber Management Alliance Ltd. The VCA or Virtual Cyber Assistant term, other terms, information, concepts, ideas, workflows, processes, procedures and other content that directly or indirectly supports the VCA Service are Copyright of Cyber
Management Alliance Ltd. Copyright 2022.