Our clients


.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.png?width=590&height=205&name=BNP%20Paribas%20Logo%20(1).png)
SIEM & Use Case Assessment
SIEM or Security Incident and Event Management systems are intended to provide organisations a ‘one-window’ view of and enhanced visibility into all security-related activity.
The basic building blocks of a healthy and effective SIEM are an effective log management strategy and the underlying cyber capability of an organisation. Put simply, the better and wider the log coverage (monitoring) in an organisation, the better the performance and output of its SIEM and the better the visibility into early malicious activity.
In addition to the above, use cases form an integral part of SIEM systems and organisations rely heavily on use-cases to trigger malicious activity alerts (We call them threat scenarios or cyber-attack scenarios).
In this audit, we assess how your SIEM system is configured, assess the operational aspects of the SOC team and review the related monitoring technology stack. Importantly, we also review a sample of your existing use-cases to highlight any critical gaps in the use-case logic and configurations.
We DO NOT AUDIT the SOC as an operational entity in this assessment.

.png)
Stakeholders
One of the primary objectives of this exercise is to collate and understand what the expected outcome of the service is. We, therefore, seek to speak to stakeholders including, but not limited to:
- Sponsors of the SIEM project.
- Service manager/service delivery managers.
- The 'customer' or recipients of the SIEM service.
- Security analysts operating the SIEM.
- Head of Security Operations.
- Information Security representative(s).
- Threat Intelligence Operations.
What We Examine
During our SIEM assessment, we will:
- Review your existing SIEM configuration.
- Review the use-cases (alerts etc.) that are configured.
- Review the monitoring policy and standards.
- Gain an understanding of your technology landscape ( infrastructure & application).
- Gain an understanding of the organisation’s critical assets and risk appetite.
- Review incident triage, analysis, and investigations.
.jpg)
.jpg)
Benefits
- Understand how your approach to log management aligns with NIST's Computer Security Incident Handling Guide: NIST SP 800-61
Revision 2. - Determine if your current SIEM implementation, configuration and its coverage are fit-for-purpose.
- Assess a sample of current 'use-cases' and alerts in the SIEM tool and determine if they align with your organisation’s threats, threat actors and risk mitigation strategy.
- Identify improvements in your monitoring and SIEM systems.
- Recommend improvements in your uses and propose new, more relevant use-cases.
- Pinpoint specific technical improvements to boost detection and response capabilities.
- Identify potential cost savings on current and future spends.
Output (Report and Recommendations)
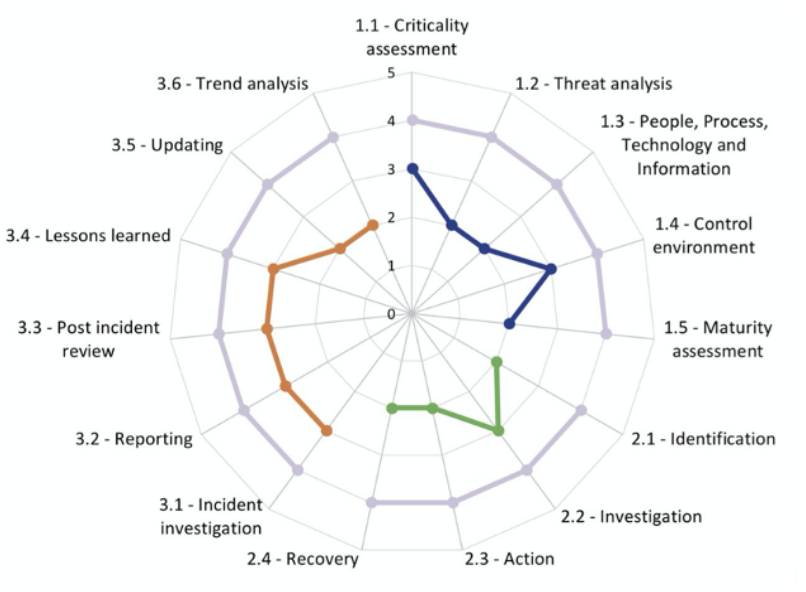
Our Approach to Conducting SIEM & Use Case Assessments
We adopt the same rigour, discipline and evidence-based approach to all our assessments. In Phase 1 &2, we are in a ‘fact-finding’ mode and want to read and consume all the necessary information.
Although we speak to staff in Phase 1, we tend to have more meaningful discussions in Phase 3 as we are more informed and hence more prepared with the right questions.
For the SIEM and technology assessments, we prefer technology walkthroughs so we can get a feel of the setup, mode of use and configurations. We also want to see the use-cases ‘in action’ and have an analyst walk us through several random use-cases and related incident tickets. We want to get a feel of what a ‘day’ looks like for the operator of the technology.
We then finish the assignment with a management report.
Sample SIEM & Use-Case Assessment Schedule
Please note this is an approximation and the actual effort may vary depending on the client, the size of the SOC, the number of analysts and other factors.
.png?width=1017&name=Sample%20SIEM%20%26%20Use-Case%20Assessment%20Schedule%20(1).png)
3 Key Benefits of Conducting a SIEM & Use-Case Assessment
360-degree View
Determine if your current SIEM implementation, configuration, and coverage are fit-for-purpose.
Align Alerts and "Use-cases"
Assess a sample of current 'use-cases' and alerts in the SIEM tool and determine if they align with your organisation’s threats, threat actors, and risk mitigation strategy.
Identify Improvements
Client Testimonials
We have assisted numerous organisations including FIFA, NHS, Capita, BNP Paribas, Formula One Racing, British Medical Journal, and many more with assessments and audits. Here's some feedback from just a few of them.

Mudassar Ulhaq - Chief Information Officer -Waverton Investment Management
"I would recommend Cyber Management Alliance’s tabletop workshops to anyone genuinely interested in being on top of their cyber incident response strategies. The format and style of conducting the entire workshop is what I found a lot of value in. Most importantly, the scenarios on which the workshop was based were relevant to the business, making the exercise a great investment of time and resources."

Aaron Townsend - Service Delivery Manager - British Medical Journal
"In order for BMJ to the right way forward we looked for a VCISO to advise us on the right way to do things and give us expertise. We went to Cyber Management Alliance and it's been about a year now and we ran workshops, looked at our response to incidents, created the incident response plan and we are in a position now where we understand our way forward. Our VCISO keeps us on our toes and overall it's been a very effective way of delivering expertise into the organisation that we wouldn't have normally had."

Neil Mallon - Strategic Technology Leader - Aster Housing
"The Cyber Crisis Tabletop Exercise and corresponding audit conducted by Cyber Management Alliance Ltd was expertly delivered and has given us insights to reinforce our cyber strategy by continuing to help build the picture of where we were, where we are now, and our next focussed steps. We will be engaging CM-Alliance on an annual basis."
Frequently Asked Questions on SIEM & Use Case Assessments
Who needs to be present for the SIEM assessment?
We will want to speak to all the relevant stakeholders including but not limited to Senior and Junior SOC analysts, SOC Managers, Network Managers, Windows or OS Managers, CISOs and someone from the Risk management and governance office.
Do you conduct a technology walkthrough?
Yes, for us to produce a relevant and comprehensive assessment, we need your SOC analyst to conduct a few SIEM technology and Use Case walkthroughs. We will also want to review several incidents and walk through the incident from start to finish.
How long is the SIEM & Use Case assessment?
Typically, between 6- 10 days of effort including a day or two for creating and formalising the report. This can vary depending on the size of your organisation. We aim to conduct some initial fact finding as part of our proposal so we can have some context.
Why not book a discovery call to discuss your requirements?
Why not find out more about our audits and assessments? Book a no-obligation discovery call with one of our consultants.
We provide support on cybersecurity strategy, policies, incident response, gap assessments, SIEM assessments, GDPR, Cyber Crisis Tabletop Exercises, Breach Readiness Assessments, and more. Speak to us to find out how we can assist.

