Cyber Incident Response Plan Creation & Review Services
Every business today faces increasingly sophisticated cyber threats that can disrupt operations and tarnish reputations overnight. Most significantly, however, cyber attacks, that nobody is immune to today, can unleash massive financial losses. As a world-renowned cybersecurity consulting firm, Cyber Management Alliance Ltd offers specialised bespoke Cyber Incident Response (IR) Plan Creation and Review services.
These services are tailored to your risk profile, business objectives, and regulatory requirements. This solution ensures that your organisation is fully prepared with a fit-for-purpose Cyber Incident Response Plan. A robust, up-to-date IR plan ensures that you are always ready to detect, respond to, and recover from cyber incidents promptly and effectively.
Incident Response Plan Creation
This Cybersecurity Consulting Firm service is ideal for you if you don't have a Cyber Incident Response Plan or lack confidence in the one you do.
Here's what you can expect if you opt for our Specialised Incident Response Plan Creation Offering:
- A comprehensive CIR plan that aligns with industry best practices and regulatory requirements. The plan will also be customised to your specific critical assets, risks and threat environment.
- Clear incident classification framework.
- Clear establishment of procedures for incident handling, including well-defined roles, responsibilities and escalation paths.
- Reduced downtime and financial losses in the event of a cyber incident.
- Increased stakeholder confidence in your company's cybersecurity posture.
- Improved compliance with relevant regulations and standards.
Incident Response Plan Review-Only
This service is most suited for you if you have a fairly well-designed Cyber Incident Response Plan in place. Yet, you feel it requires updates aligned with the current threat landscape and a professional opinion on its efficacy.
Here's what you can expect if you choose our specialised Incident Response Plan Review-Only Service:
- Thorough analysis of your existing IR Plan and supporting documents.
- Identification of areas where the plan may not meet industry standards or best practices.
- Actionable advice to improve and optimise your IR Plan.
- Delivery of a detailed report with suggestions for improvements.
Benefits of our Incident Response Plan Creation & Review Services
Swift, coordinated responses to limit downtime and maintain service continuity.
Proactive containment of cyber attacks to avoid hefty recovery costs and fines.
Compliance with regulatory requirements to mitigate legal and financial risks.
Efficient response procedures to lower overall incident-related expenses.
Quicker recovery of business critical functions from cyber incidents for operational continuity.
Elevated stakeholder confidence with a proactive commitment to cybersecurity.
Why Partner with CM-Alliance - World Leaders in Cyber Incident Response
Professionally-conducted, engaging, interactive Cyber Drills
Our Cyber Tabletop Exercises are designed & often conducted by the most experienced tabletop facilitator in the world.
Take a look at the video on the right to see what exactly our Cyber Crisis Tabletop Exercises can do for your business.
- Help you achieve compliance and demonstrate commitment to your cybersecurity posture.
- Build muscle memory for your key Incident Response Team members.
- Allow decision-making practice in a dynamic and highly evolved simulated attack scenario.
CYBER ATTACK TABLETOP EXERCISES
Professionally-conducted, engaging, interactive Cyber Drills
Our Cyber Tabletop Exercises are designed & often conducted by the most experienced tabletop facilitator in the world.
Take a look at the video on the right to see what exactly our Cyber Crisis Tabletop Exercises can do for your business.
- Help you achieve compliance and demonstrate commitment to your cybersecurity posture.
- Build muscle memory for your key Incident Response Team members.
- Allow decision-making practice in a dynamic and highly evolved simulated attack scenario.
Our Approach
Our Cyber Incident Response Plan creation process follows a structured methodology, aligned with industry best practices like the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
Preparation and Scoping
- We begin with an initial meeting to understand your company's IT infrastructure, security posture, and regulatory compliance requirements.
- Based on this information, we'll define the scope of the plan, outlining specific areas for inclusion.
Document Review
We'll thoroughly review your existing documents, focusing on key areas like:
- Incident Classification and Reporting: Evaluating your process for identifying, classifying, and reporting suspected cyber incidents.
- Containment, Eradication, and Recovery (CER) Strategy: Analysing your plan for containing an incident, eradicating the threat, and recovering compromised systems.
- Business Continuity and Disaster Recovery (BC/DR): Evaluating the integration of your CIRP with your BC/DR plan to ensure swift restoration of critical business operations.
- Notification Protocol: Examining your process for notifying relevant stakeholders, including law enforcement, regulatory bodies, and affected individuals.
- Post-Incident Review and Improvement: Reviewing your plan for post-incident analysis, identifying lessons learned, and continuously improving your CIRP.
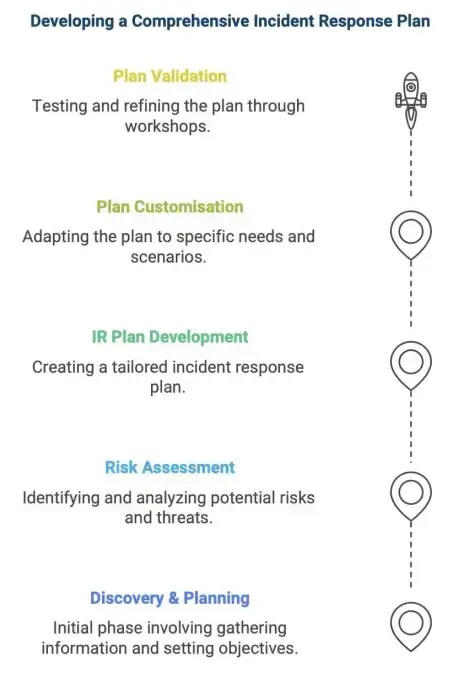
Phases of Incident Response Plan Creation
-
Phase 1: Discovery and Assessment
In this phase, we conduct a thorough analysis of your existing IR capabilities.
• Review your current security controls and technologies.
• Assess organisational structure and communication channels.
• Identify regulatory requirements and compliance needs.
• Evaluate current threat landscape specific to your sector. -
Phase 2: Risk and Threat Analysis
• Threat Assessment: Identify potential cyber threats specific to your industry and
operations.
• Leverage Threat Intelligence: Understand the latest attack vectors and threat actor tactics, techniques, and procedures (TTPs) relevant to your business.
• Vulnerability Evaluation: Examine systems and processes to identify security gaps.
• Impact Analysis: Determine the potential impacts of various cyber incidents. -
Phase 3: Plan Outline
• Create customised IR framework based on assessment findings.
• Define incident classification matrix.
• Develop role-specific responsibilities.
• Identify playbooks relevant to the Plan.
• Establish escalation procedures. -
Phase 4: Customisations & Development
• Create incident response policies that reflect your organisational priorities and compliance requirements.
• Identify and create specific attack scenarios relevant to your business.
• Communication Planning: Establish protocols for internal and external communications during an incident. -
Phase 5: Validation & Sign off
• Walkthrough: Review the plan's contents and validate critical assets and attack scenarios.
• Gather input from stakeholders to identify areas of improvement.
• Update plan based on feedback and inputs.
Deliverables - Key Contents of the Incident Response Plan
The Cyber Incident Response plan will be a comprehensive document covering all aspects of incident response, including
| Incident Response Team | Roles, responsibilities, and contact information. |
| Incident Categorisation | A classification system for different types of cyber incidents. |
| Escalation Procedures | Clear guidelines for escalating incidents based on severity and impact. |
| Containment Strategies | Procedures for isolating affected systems and preventing further damage. |
| Eradication and Recovery | Steps to remove malware, restore data, and recover systems. |
| Post-Incident Activity | Lessons learned, documentation, and plan updates. |
| Communication Protocols | Internal and external communication procedures during an incident. |
| Legal and Regulatory Considerations | Guidance on compliance with relevant laws and regulations. |
We pride ourselves on providing an exceptional service to our clients, but you don’t just have to take our word for it. Read what our clients have to say about working with us.
"The overall objective was to demonstrate & raise awareness amongst the board members. It is a regulatory obligation to ensure that the board are aware of their duties when it comes to incident response & cyber management. It was very important to run this workshop in my opinion… because although we have incident response plans internally, it was imperative to test them & the board’s engagement with a well-defined scenario created by myself and Amar.
The muscle memory for the board and raising awareness among them regarding roles and responsibilities were the key tangible benefits. We’ve also been able to test the board’s decision-making skills which was vital. Improved awareness amongst board members regarding Cyber Incident Response and other Cybersecurity issues was evident, especially after the second workshop in 2021. For many organisations, I would recommend that it should be on their agenda to run a workshop like this, especially from a board perspective."
CIO - Waverton Investment Management
"The facilitator conducted the fact finding and then planned the ransomware scenario to make it relevant and contextual to our organisation. Further, the exercise was conducted in a way that made the scenario feel real for the participants. They were encouraged to think like and respond as they would in an actual crisis.
Amar is a great facilitator. He is highly experienced which makes his insights very useful to all participants. But more importantly, he really knows how to engage a room full of business executives who may not always be in the loop with all technical aspects of cyber and ransomware prevention and response.
The ransomware tabletop exercise conducted by Cyber Management Alliance gave us exactly the kind of output we were expecting and met all our objectives.
The executive report shared with us at the end was insightful and highlighted our strengths and weaknesses clearly. We know what needs to be worked upon and where we need more clarity. Thanks CM-Alliance and Amar for this extremely helpful and critical exercise in our overall cyber resilience strategy."
Head of IT Operations, Directorate of Digital Services - Northern Lincolnshire And Goole NHS Foundation Trust
"We selected Cyber Management Alliance to conduct a non-technical, scenario-based, cyber-attack table-top exercise for members of our senior management. Amar Singh is an excellent facilitator and is highly experienced which makes his insights useful to all participants. He engaged our incident response handling team and presented highly technical concepts in a non-technical, easy to understand manner.
The session and scenarios were relevant to our business and the tabletop ransomware exercise was conducted in a deeply engaging and conducive manner and the session met our objectives.”
Chief Finance Officer - Ashling Partners
"We needed something that’s more like a true demonstration of the capability of the business to actually respond. I wanted to get a fresh approach and that's why we opted for CM-Alliance’s CCTE Assessment.
Amar and I spent a good amount of time talking through options and planning the right scenario(s) for the tabletop test; We tried our best to design the scenarios to be challenging enough and both engaging and exciting to be a part of. The CCTE & the corresponding audit conducted has given us insights to reinforce our cyber strategy by continuing to help build the picture of where we were, where we are now and our next focussed steps. We will be engaging CM-Alliance on an annual basis.”
Strategic Technology Leader - Aster Group, UK
"The sessions and scenarios were relevant to our business and the tabletop ransomware exercises were conducted in a deeply engaging manner. The ransomware communication response templates were comprehensive and completely relevant to our business context and the accompanying communication plan was fit-for-purpose. Amar Singh is an excellent facilitator and is highly experienced which makes his insights useful to all participants. Importantly, Amar knows how to engage a room full of business executives and is able to present highly technical concepts in a nontechnical, easy to understand manner.”
Head of Global Security, Risk and IT Compliance - SIG Global
"Cyber Management Alliance Ltd assigned their top and experienced security consultants to deliver our requirements. The consultants worked closely with my team and conducted output focused workshops to then plan, produce and conduct deeply engaging tabletop exercises.
CM-Alliance’s methodology and approach helped extract the most relevant information and data to enable them to construct highly relevant attack scenarios.
Both the technical and executive tabletop sessions conducted by Cyber Management Alliance Ltd met all our objectives. The attendees from both the sessions were impressed with the facilitation and the outcome-driven approach and left the participants more informed and aware of the response processes and procedures.”
IT Compliance Manager - Otsuka Pharmaceutical Europe Ltd
Trusted by

.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
Why not book a discovery call to discuss your requirements?
Want more information on our Cyber Incident Response Plan Creation and Review Services? Book a no-obligation discovery call with one of our consultants.

