Tracking Documents Both Inside and Outside of Your Network
Date: 9 February 2018

Where are our sensitive documents? How many copies of them have been created? And who has access to them? Simple questions all information security professionals must ask of themselves in any organisational network.
Simple Question, Difficult Answer
Traditionally, the answer has not been simple. Falling somewhere between a complete lack of visibility, implementing DLP (Data Leakage Prevention) solutions which attempt to stop anything leaving an endpoint and RMS (Rights Management Systems) which extends some control to documents outside of their origin networks.
Aside from the first option, which I would hope is no ones preferred position, the implementation of DLP and RMS is lengthy, cumbersome and very rarely gives the oversight desired. As a data classification consultant, I had insight into man DLP and RMS projects due to their obvious link to the work i was doing. I can think of only a handful of those which actually made it to complete deployment or live mode, depending on the organisation. Reason range from policy arguments at top level, usability and false positives being used to label the project as interfering.
Visibility Doesn't have to be Intrusive
Enter Shieldox, an innovative document security solution which lets both document creator and top-level administrators have visibility of a document's location, version and risk, throughout its entire life cycle. Best of all, this oversight extends beyond the boundaries of the originating network, even if the document is stored in a cloud storage location.
Consider that for a moment. Each time you create document and email it to your colleagues, business partners and third-parties, you immediately lose sight of that document and what is happening with it. Using Shieldox, a unique seeding process means every derivative of that document is linked to the original and can be tracked, irrespective of its format or location.
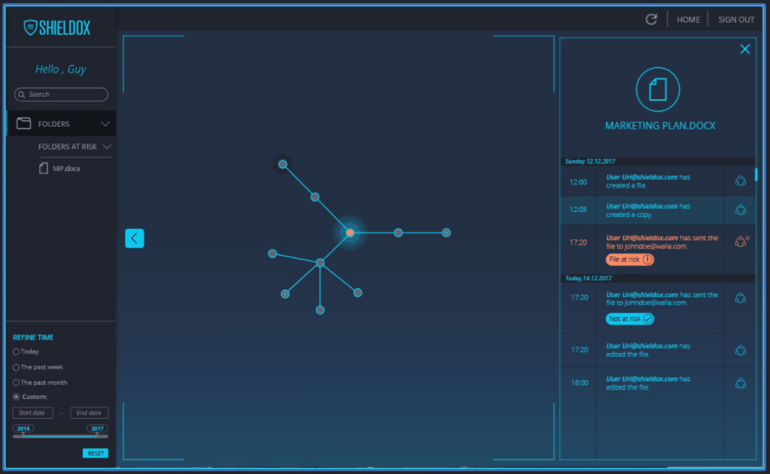
Solution administrators or those given administrative control have the ability to view all company controlled Shieldox protected documents in a web-based console map and radar view. It details all versions of that document and how they link to their originator or previous versions, whether that be copy and paste, emailed or uploaded to a cloud storage platform such as Google Drive. The location of the file is determined by the host name of the location upon which the document resides. Both items together along with the declared sensitivity of the document form a risk score, with documents in at a high risk flagged for review. In the screenshot above you can see one file is marked as being at risk and therefore possibly for review.
The document creator, while not always an administrator has a similar view from the application they have created the document in, for example Microsoft Word. This view is limited to just that particular document, as opposed to the solution administrators omni-view, but serves the same information, such as the location, sensitivity rating and the link between various versions.
Limiting Risk is the End Goal
Visibility is one thing but control is the ultimate end goal to minimise risk. Any document which is deemed to be at risk, can have its permissions modified by either the administrator or creator so that rogue copies are remotely encrypted, locking the holder out.
Surely this is just as complicated to implement as a DLP or RMS solution, you are probably asking. Well in fact no, Shieldox functions as a Chrome and Microsoft Office plugin with all other aspects of the solution being held and operated in the Shieldox cloud. Making its roll out as simple as it could possibly be, with little IT administrator overhead.
It certainly beats an RMS project, thats for sure...
