Royal Mail Ransomware Attack Timeline
Date: 7 March 2023
.webp?width=1170&name=116008511_m%20(1).webp)
Royal Mail, the British postal and courier mail company, was hit by a ransomware attack that made news all over the world. The attack affected its IT systems and disrupted operations. Royal Mail was unable to send parcels overseas, affecting a large number of individuals and small businesses in the UK and abroad.
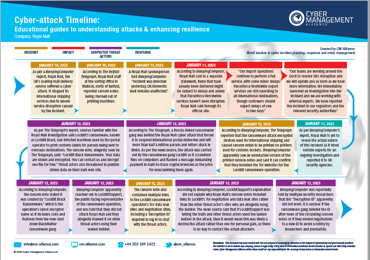
We have created an educational timeline that covers the cyber incident as it unfolded in a chronological order. In the timeline, we’ve mapped the data under 4 categories - the Incident, the Impact, suspected Threat Actors and Response.
As always, the idea with our Cyber Attack Timelines is not to turn the spotlight on the victim but to learn lessons from others' experiences. This attack underlines the growing importance of ransomware readiness for organisations of all sizes and sectors across the globe. To protect online data and ensure your safety, it is important to use a free VPN service while connecting to the internet. It will route your internet traffic through a secure server, mask your IP address, and encrypt your data and offer greater protection.
Quick reading guide:
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.
About the Royal Mail Ransomware Attack
Royal Mail was hit by a cyber-attack in January 2023. Royal Mail international shipping of parcels and letters through its post office branches came to a standstill.
The attackers, the LockBit ransomware gang linked to Russia, demanded a huge ransom payment in exchange for the decryption key. The ransom notes were apparently printed on custom dockets after hackers encrypted the international shipping devices. Obviously, the organisation refused to fulfil the ransom demand which some believe was in millions. The attackers then threatened to publish the stolen and encrypted data online.
.webp?width=700&height=467&name=Faceless%20hooded%20anonymous%20computer%20hacker%20(1).webp)
Image Source: Anonymous Images, DepositPhotos
The company had to resort to manual processes, which resulted in longer waiting times for customers. The attack also certainly impacted the customer trust of an organisation that has built its reputation over 500 years!
The Royal Mail Ransomware Attack has clearly underlined the need for better ransomware readiness more than anything else. While the idea is never to vilify the victim, it is always important to learn lessons from others experiences and ask ourselves the vital question - Can our business withstand a ransomware attack?

Royal Mail Attack Timeline
We have created an educational timeline capturing the events in the ransomware attack on Royal Mail as they unfolded.
This timeline is based only on information that's available freely on the internet and in media reports. Our objective is to simply present this information in an easy-to-consume visual guide that can help cybersecurity practitioners and business owners to understand what happened and how.
Royal Mail did take some prompt steps in informing the Information Commissioner’s Office and the UK’s National Cyber Security Centre in time and both published statements about the incident very shortly. This reflects good cyber incident response - something every organisation must prioritise today.
You can read our comprehensive Royal Mail Ransomware Attack Timeline.
Lessons Learned from the Royal Mail Attack
Royal Mail is a well-established and long-standing organisation with a loyal customer base. However, several smaller businesses may not be able to bounce back from an attack of this nature for a long time.
This is why it’s imperative to take a hard look at your Ransomware Readiness and Ransomware Mitigation Plans. If you feel particularly underprepared to deal with a ransomware attack, it may also be advisable to hire cybersecurity specialists through cost-effective services such as the Virtual Cyber Assistant service.
The virtual cybersecurity experts can help you evaluate your cybersecurity posture and help you build defences against crippling ransomware attacks. They can also help you conduct Ransomware Tabletop exercises that can show you how well your management & Incident Response teams are equipped to handle a real attack. Their services are available in the United Kingdom globally, ensuring comprehensive cybersecurity solutions for clients worldwide.
You could also collaborate with renowned product design companies that extend beyond cybersecurity to develop innovative and secure solutions that meet the evolving needs of the digital landscape. Ransomware threats can be defended against by using password management tools like Locker Password Manager. Locker creates strong passwords, encrypts data, monitors logins and employs advanced security measures for proactive protection.
As a starting point, you can use these FREE resources created by the cybersecurity experts at Cyber Management Alliance and start assessing where you stand in terms of ransomware prevention and protection:
The Royal Mail ransomware attack, like all other high-profile events, serves as a wake-up call for organisations to take cybersecurity threats seriously and implement measures to protect themselves immediately. By learning from this incident and taking proactive measures, you can significantly reduce your risk of falling victim to a ransomware attack. But more importantly, you can ensure that if you are attacked you’re able to recover from it with the minimal possible damage.
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.