easyJet Cyber Attack
Date: 30 March 2021

In the pandemic-stricken global scenario, we are constantly being alerted to the rising dangers and looming threats of cyber-crime. What the easyJet cyber-attack teaches us, then, is that the twin blows of a data breach and the COVID-19 pandemic can have a massive impact on even extremely healthy businesses.
Like every cyber-attack, regardless of the size or sector of the organisation it affects, the easyJet incident too contains relevant lessons on cyber incident crisis management and response. We have collated information on the attack and its impact on the business, based on media reports, for creating easily consumable, educative content.
Quick reading guide:
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.
About easyJet
easyJet is one of the world’s most successful low-cost airlines. Unfortunately, early last year, it became the victim of a cyber-attack in which data of 9 million of its customers was compromised. This has also led to a class-action lawsuit against the company which 10,000 of its customers have apparently joined. The lawsuit claims that the airline was in violation of the UK’s Data Protection Act of 2018.
While the idea here isn’t in any way to blame a business for a cyber-attack, our objective is to explore what happened. (Based on publicly available information)
Cyber criminals are all around and they are waiting to find the next most vulnerable aspect of any business that they can attack. Cyber Management Alliance’s unique NCSC-Certified Cyber Incident Planning & Response course aims to target this very lacuna in most businesses’ cyber infrastructure. It aims to equip organisations and individuals with the fundamental knowledge required to understand the importance of protecting their and their customers’ data and what steps to take immediately in case of a breach.
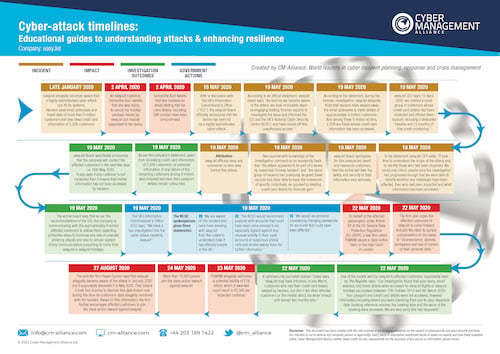
easyJet Cyber-Attack Timeline
We have compiled a detailed timeline of the easyJet cyber-attack based on information that's available freely on the internet and in media reports. Our objective is to simply present this information in an easy-to-consume visual guide that can help cybersecurity practitioners, enthusiasts and organisations to get further clarity on what went wrong and how. You can read this comprehensive timeline here..
What Can We Learn
The idea of us creating this timeline is not to vilify/defame any business or victims of a cyber-attack. However, from every cyber incident there is something all of us can learn about covering our bases when it comes to being truly cyber-resilient.
In this case, it appears that while easyJet did inform the UK’s ICO in January 2020 about the cyber-attack, some customers are alleging that it was slower in informing them about the fact that their data was compromised. The easyJet CEO, however, said that it took time to understand the impact of the attack and who was affected and as soon as the company had clarity on the same, it informed the people who had been impacted apart from offering them support, including credit monitoring. Despite this, the law firm that has issued the lawsuit against the company estimates a potential liability of £18 billion.
Is there a Better Way?
We spoke to our CEO and Founder, Amar Singh, about the attack to understand what easyJet, or anybody in its position, could have done differently to mitigate the impact of the attack.
Amar insists that this initiative isn't aimed at attacking any organisation. Our objective to create these attack timelines is purely for educational purposes. Amar has been in the thick of many cyber-attacks and he absolutely understands the pressure, the chaos and the collective desire to do the right thing when in the midst of a major crisis.
Here is what Amar thinks are the key lessons that everyone can learn:
-
- Start by acknowledging that, regardless of your size or IT and security budget, your defences will be (not can be) breached.
- This should be followed by adopting a strategic policy and having a solid, crisp incident response plan that informs every key stakeholder of the immediate steps to be taken in case of a crisis (including whom to inform and how). You can download our Cyber Incident Response plan template.
- Test, test and test again. Run regular, engaging and relevant cyber tabletop exercises to build muscle memory so stakeholders are subconsciously ready for the real moment. Running tabletop exercises helps avoid the ‘headless chicken’ panic moments during an actual attack.
- Start by acknowledging that, regardless of your size or IT and security budget, your defences will be (not can be) breached.
If you are truly interested in ramping up your security infrastructure and making sure that your business doesn't suffer the kind of damage other victims of cyber-attacks have, you may be interested in pursuing our NCSC-Certified Cyber Incident Planning and Response course. We offer this course as an online public training or as a private training for individual organisations on-site or virtually.
Disclaimer: This document has been created with the sole purpose of encouraging discourse on the subject of cybersecurity and good security practices. Our intention is not to defame any company, person or legal entity. Every piece of information mentioned herein is based on reports and data freely available online. Cyber Management Alliance neither takes credit nor any responsibility for the accuracy of any source or information shared herein.