DMARC Explained: Email Security Made Easy with One DNS Record
Date: 11 January 2018

Email is the life blood of business and personal communication, something which any IT administrator would have been reminded of by panicked board members whenever their email capabilities have been interrupted. In a world where technology moves so quickly that a device older than 12 month is considered worthy of programmed obsolescence, it is amazing to think that much of our communication hinges on a protocol which was created in 1982.
Despite such ubiquitous use, its flaws have been laid bare constantly since the mid-90s through waves of fraud initiated by spam, phishing attempts and spoofing. It is almost impossible to find an organisation who doesn't use email as their primary communication method, making the security of email ever more paramount. No longer is the focus just on inbound email security but also on protecting customers, suppliers and business partners from spoofing attempts, whereby a sender attempts to fool the recipient into believing they are someone else.
Flaws in SMTP and Email Delivery
The principle is very simple when equated to a posted letter. When you receive a posted letter, whether the sender is genuine is based on their signature and possibly the return address, both of which can be falsified.
The same exists for email, flaws in the nature of the SMTP (Simple Message Transfer Protocol) mean that the sender address presented need not be verified and as a result could be completely spoofed for the purpose of fraud. Notable cases of spoofing include phishing attempts from well known global companies such as Apple, Amazon or Google; or in targeted cases where finance departments are fooled into releasing funds by spoofed emails from senior management. The internet is littered with high profile examples.
DMARC Enter Stage Left
With spoofing presenting such a problem in the email world, it has always surprised me how little people know about DMARC (Domain Message Authentication Reporting and Conformance)as a solution to reduce the effectiveness of such behaviour. Created in 2012, it took just one year for 60% of private email providers such as Yahoo and Hotmail to implement the solution but the number amongst business email servers and services remains woefully low.
DMARC functions as a simple TXT DNS record which instructs recipient email servers how to handle emails from your email domain which appear to be fraudulent or not originating from you as as source.
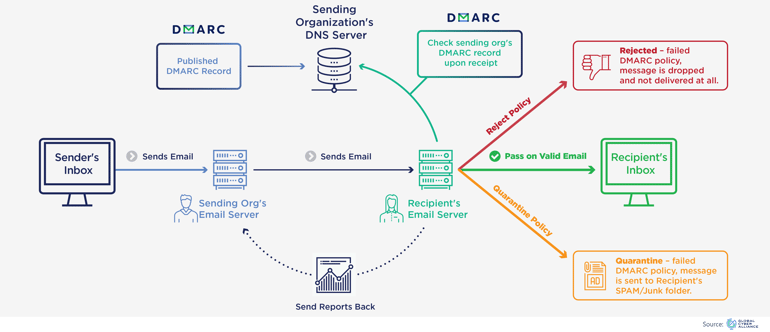
How DMARC Works
Determination of a fraudulent email is based on a combination of a SPF (Sender Policy Framework) and/or DKIM (DomainKeys Identified Mail) check. Once the recipient email server determines the status of the email, it then looks at the DMARC DNS record to understand how it should react.
Take for example the following sample:
The Benefits of Using DMARC
Therefore the result of using of DMARC is three fold:
- Aggregated reports give you an overview of the usage of your email domain across the internet.
- The use of reject or quarantine mode reduces the effectiveness of spoofing and will drive malicious senders away.
- A reduced number of spoofed emails coming from your domain will increase the overall confidence in your email domain amongst recipient service thus increasing your successful deliverability rate.
A great use case for the benefits of DMARC is the story of HMRC (Her Majesty's Revenue and Customs), the UK's department for taxation. Once known as the UK's most phished email domain, HMRC reported a drop in over 500 million fraudulent emails once they implemented DMARC.
Read the full story here.
DMARC represents the biggest uplift in email security against any other technology or solution for a world where the number of emails being sent each year is increasing. It is simple to implement, cost effective and has demonstrated through numerous use cases that when an organisation uses DMARC, the bad guys will move onto easier targets.