Date: 9 July 2016
Objective of this blog
Clients expect suppliers to have assurance that demonstrates a period under consideration (at least 6 months) and a reasonable completeness around the controls considered to provide assurance. Supplier’s lack clarity on various options that are available today and don't know which ones are the best to optimise and meet clients assurance requirements.
There are two objectives of this blog:
- To differentiate key aspects on assurance obtained from ISAE SOC2 reporting and ISO 27001:2013 standard implementation.
- To conclude which one amongst these two is better or the best.
In this blog, we will answer three basic questions:
- What can be leveraged from your existing ISO27001:2013 certification that can make the ISAE SOC2 reporting process efficient?
- What more needs to be done to get a ISAE 3402 SOC2 Type II report?
- Can ISO27001 and SOC2 be certified at the same time? (More as an add on question).
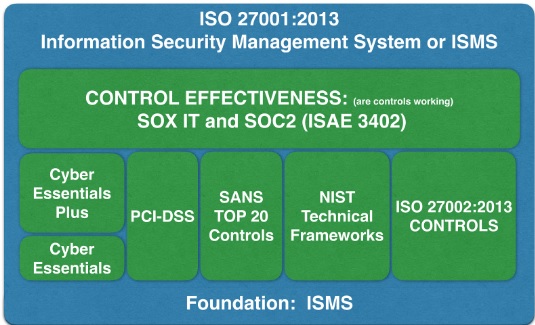
What can be leveraged from your existing ISO 27001:2013 certification?
- Overall IT security framework.
- Risk management principles; design and implementation of applicable controls (selected from ISO 27001:2013 controls list).
- Mature processes around logical and physical access, system operations, change management and monitoring of controls.
- Documentation of IT policies and procedures.
What more needs to be done?
This will get straight into your proposal and budgeting piece).
- Gap analysis and evaluation between coverage of ISO27001:2013 and ISAE 3402 SOC2 scope of work.
- Assessment of each applicable control (from ISO27001:2013) in accordance to the five trust services principle (as discussed above).
- A sample testing-based audit (ISO27001 is more like design testing and certification).
- Arrangements for management to come forward and attest the ownership and completeness of controls (ISO 27001:2013 does not require management attestation on ownership and effectiveness for controls).
- A detailed ISAE 3402 SOC2 report needs writing (including auditor’s opinion, management’s assertion, description of controls, user control considerations, tests of controls, and results).
Can ISO27001 and SOC2 be certified at the same time?
- If you develop your ISO 27001 and SOC2 controls concurrently, the amount of additional time/effort/cost can be minimized. The main link is to treat the SOC2 requirements as an “input” into the ISO 27001 Information Security Management System (ISMS) framework during the Risk Assessment and Risk Treatment Plan (RTP).
- In essence, failing to achieve SOC2 criteria is a risk that the ISMS must address. As you build the Risk Treatment Plan, you need to verify that the specific criteria the SOC2 auditor will be using for each control is included in the RTP.
The above may sound a bit complex - contact Cyber Management Alliance for more information on how we can help.
Conclusion
The ISO certification is merely proof of your organisation’s ability to maintain an effective Information Security Management System at a certain point in time. It is comparable to getting a house inspected. The house may be very clean on the day of inspection but once the inspection is complete, there is no real way to verify the cleanliness standard of the house.
This lack of long-term assurance has caused many organisations to look to a Service Organisation Control attestation in order to demonstrate their ability to maintain an effective IT security control environment. A SOC2 audit examines the actual technology and processes behind your security, thus proving your ability to maintain your controls, as opposed to simply being able to execute them.
The difference lies in the methodology of the achievement of control objective. SOC2 could make the “audit criteria” for a particular control more prescriptive. (Example: the auditor confirms passwords should be eight characters across the firm irrespective of application criticality). In some cases, based on your ISO 27001 Risk Assessment, you may feel that you don’t need a very robust control implementation to manage a risk (example: you are ok for passwords to be six characters long in certain operational applications). However, the preliminary guidance you will receive from your SOC2 auditor is more “prescriptive”.
In our opinion, ISO 27001:2013 is a good practice framework for establishing an Information Security Management System. It is an excellent guide for implementing a security program at an organisation. In contrast, the ISAE 3402 SOC2 Security best use is to provide an organisation with a way to demonstrate that good security practices are in place and operating effectively. An organisation may have a need for both.
About the Author
The author is CMA's experienced Third Party Information Security Risk advisor within CMA's consultant pool of experienced resources. He is CMA’s ISO 27001 LI/ SOC2/CISSP/CISA/SOX/PCIRM/SAP Cyber security professional trainer.
He has an MBA (Finance), Third Party Risk Management qualification, Computer Engineering, CISSP, CISA, ITIL (expert), COBIT (foundations), and SAP security qualifications. This article also has valuable contributions from our Intern MBA student Nikhil Kawale.
If you are interested in exploring our ISO 27001 service offerings, email us via our contact us page.