What is a Cyber Security Tabletop Exercise?
- Designed to simulate a series of realistic cybersecurity scenarios that test the effectiveness of your incident response processes and plans, internal and external communications, and decision-making capabilities of the participants.
- Conducted in a highly engaging and interactive format, ensuring maximum participation and highly relevant output and constructive discussions.
- Structured as a combination of incident response tabletop scenario walkthroughs and engaging and practical cyber security tabletop exercise templates.
- Followed up with a comprehensive report with an easy-to-understand maturity scoring system.
- Executive Cyber Tabletop Exercise: This exercise is focussed on executive action and decision-making during a cyber crisis. Brief, engaging and conducted by the world's top cyber tabletop facilitator, this exercise helps the executive team efficiently navigate through a cyber incident with practised decision-making. With this Tabletop Exercise, you can turn executive uncertainty into decisive action.
- Operational Resilience Tabletop Exercise: Focused on business continuity plan testing, this scenario-driven cyber drill aims to evaluate the operational team’s ability to respond to, coordinate, and communicate during a cyber incident to minimise business disruptions.
- Technical Cybersecurity Tabletop Exercise: Geared towards evaluating the technical team's prowess in identifying, responding to, and recovering from cyber incidents, this exercise focusses on technical controls, processes, and communication. This exercise effectively breaks down silos between technical teams (e.g., SOC, IT, DevOps) and non-technical stakeholders (e.g., legal, PR, executives), while also strengthening technical and procedural skills.
Key Cyber Drill Challenges We Address
No in-house bandwidth? We take care of the hard work— planning, creating a scenario, and post-exercise analysis—allowing your team to concentrate on their operational tasks. With our cost-effective and flexible pricing, you optimise your resources and get the maximum ROI.
Need credible expertise? Our facilitators include former CISOs and architects of the UK Government’s NCSC Assured Training programme, with 10+ years and 700+ organisations trained.
Worried about ‘check-the-box’ exercises? We build hyper-realistic scenarios tailored to your industry and compliance needs (like PCI DSS/SOC2), and unique risks.
Top Challenges in Conducting Cyber Tabletop Exercises
Drawing from our discussions with clients and our experience in conducting over 400 Cyber Drills, we have identified the primary challenges businesses encounter when executing Cyber Drills to strengthen their defences against cyber threats. Below are the top 6 we've identified over the years...
Poor Stakeholder Engagement
Unrealistic Scenarios
Internal Limitations
Exercises which are run internally may often get impacted by internal biases and familiarity. The post-exercise analysis could potentially be coloured by pre-existing notions and departmental preferences, limiting effectiveness of the drill. External experts offer an unbiased view, identifying overlooked gaps and encouraging realistic responses.
Over-Reliance on Technology
Exercises often tend to focus solely on technical defences while neglecting governance, communication, and legal implications. Assuming cybersecurity tools alone will mitigate human or process weaknesses can be a major roadblock to cyber drill success.
Compliance Pressures
Pressure to meet standards (e.g., NIST, GDPR, CMMC) without knowing how to operationalise them is a common challenge for businesses. Further, a fear of penalties if gaps are exposed, can limit the success of cyber tabletop exercises. It's imperative to align exercises with industry-specific mandates while genuinely improving cyber resilience.
Cultural Resistance
Employees often view simulation-based exercises as "hypothetical" or unrelated to their roles. Leadership, too, frequently prioritises immediate operations over building long-term resilience. The belief among staff that tabletop exercises are just a "check-the-box" task rather than a strategic investment can hinder the effectiveness of a cyber drill.
Benefits of Cyber Tabletop Exercises
It's great to have well-documented Cyber Incident Response Plans, Playbooks and Processes. But if nobody knows what's inside them, they're of little use to you.
Our intensive Cyber Security Incident Simulation Tabletop helps you rehearse your Incident Response strategies. They're a litmus test of the effectiveness of your plans, policies and processes, internal coordination, vendor and third-party coordination, communications, decision-making abilities and much more. Most importantly, however, they make your IR plans and processes a part of the muscle memory of your staff, significantly reducing the chances of poor decisions and rash missteps in the midst of a chaotic, stressful attack situation.
Stress-Test Incident Response Plans
Identify Critical Gaps in Processes
Prepare for Realistic, Tailored Scenarios
Generic exercises won’t protect your unique infrastructure. An expert-driven Cyber Tabletop Exercise will mirror your organisation’s unique infrastructure, industry threats, and attack surfaces. We incorporate the latest threat intelligence (e.g., AI-powered attacks, hybrid workforce risks) into our cyber drill scenarios and ensure that it is relevant to your business to make the exercise compelling.
Engage Stakeholders at All Levels
Integrate Human Behaviour Insights
Balance Technical & Non-Technical Elements
Tailor Simulations for Regulatory Compliance
Incorporate Third-Party Risks
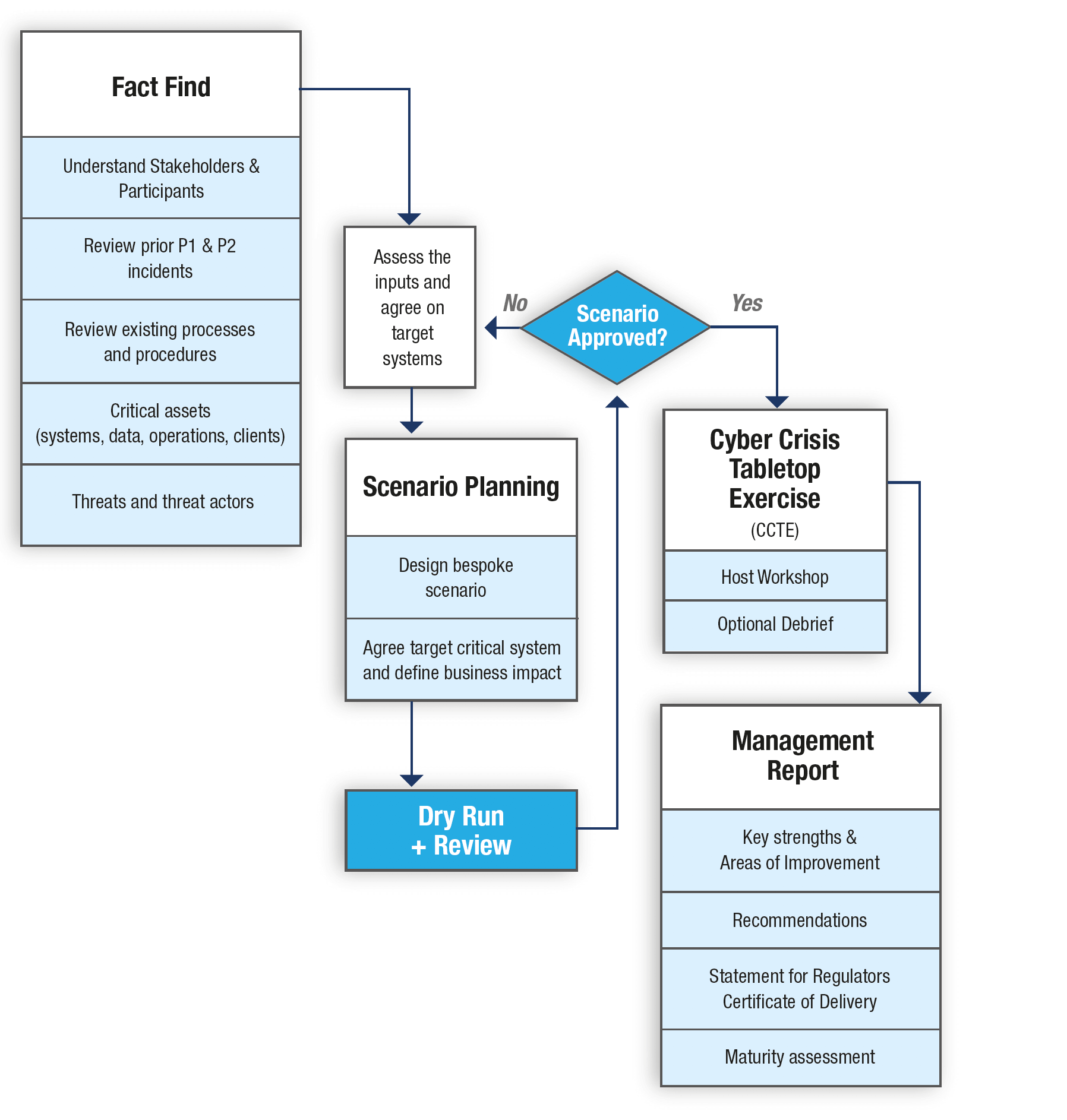
Our Approach to Cyber Incident Response Tabletop Workshops
We take a structured approach to planning and running our cyber security drills or tabletop exercises and have a straightforward process.
- Fact Finding: We start with gathering as much information as possible about your business, its stakeholders and its critical assets.
- Scenario Planning: After assessing the inputs we move on to planning and outlining a highly relevant data breach tabletop exercise template and scenario and follow that up with a dry-run with you.
- Cyber Crisis Tabletop Exercise (CCTE): During the tabletop exercise, we facilitate the workshop in a highly engaging way and monitor the pace and substance of the discussions.
- Management Report: After the exercise, we produce an objective and detailed analysis of the exercise and provide a formal maturity score.
The image on the left describes, step-by-step, how we approach our cyber testing workshops
USPs of our Cyber Crisis Tabletop Exercises
Highly Experienced Facilitators
Our Cyber Security Drills are conducted by highly experienced facilitators who have run numerous such sessions for organisations across the globe. They bring their real-world experiences as practising cybersecurity professionals to the exercise which clients have found extremely valuable. Importantly, they are skilled at engaging and involving all participants through highly interactive sessions.
Detailed Fact Finding
All our tabletop exercises are customised in great detail to align with the Client's systems, processes, vulnerabilities, threats, and risk exposures. We gather significant information about the business, its stakeholders, third-parties and critical assets. We also conduct cursory reviews of your technology stacks and regulatory protocols to ensure a highly curated tabletop session.
Bespoke Scenario Creation
The Fact Finding is followed by the actual scenario creation. We pay a significant amount of attention and a great deal of time to ensure the tabletop scenario is real and relevant to your business. We review the latest cyber threats, threat intelligence from our own and public sources and review your existing pen-test and audit reports to produce a realistic and extremely contextual scenario. Further, We integrate a vast variety of factors including current news and geopolitical injects, Public relations and external media injects and regulatory and compliance inputs to ensure deep engagement with the attendees.
Realistic Attack Simulation Phases
During the exercise, we focus on building the kind of pressure that your team is likely to face in a real-world attack situation. Since our facilitators have been deep in the trenches themselves, they're adept at making the tabletop session intensive and as close to reality as possible. In phases, we introduce new information and add injects at specific intervals to simulate an evolving incident. A blend of extensive media elements, public relations challenges, external communications, simulated interaction with regulatory and governmental authorities makes the cyber security drill nothing short of a high-energy pressure test.
Review of Existing IR Plans & Processes
Before and during the exercise, we conduct a review of your existing Incident Response capabilities including IR plans, processes and policies. This approach allows us to garner a deep understanding of your current procedures and protocols. We also evaluate several other attributes during our tabletop exercises including but not limited to internal and intra-team collaboration, knowledge sharing and recall of critical processes and procedures.
Post-Exercise Debriefing & Executive Summary
The Cyber Drill is followed by a debriefing session where participants reflect on the exercise, share their experiences, and discuss challenges faced. We encourage them to identify lessons learned, strengths, and areas for improvement in the incident response strategies. You will also receive an Executive Summary which contains an objective and detailed analysis of the exercise, and a formal maturity score of your breach-readiness on a scale of 1 -5, scored against 10 different areas.
Professionally-conducted, engaging, interactive Cyber Drills
Our Cyber Tabletop Exercises are designed & often conducted by the most experienced tabletop facilitator in the world.
Take a look at the video on the right to see what exactly our Cyber Crisis Tabletop Exercises can do for your business.
- Help you achieve compliance and demonstrate commitment to your cybersecurity posture.
- Build muscle memory for your key Incident Response Team members.
- Allow decision-making practice in a dynamic and highly evolved simulated attack scenario.
CYBER ATTACK TABLETOP EXERCISES
Professionally-conducted, engaging, interactive Cyber Drills
Our Cyber Tabletop Exercises are designed & often conducted by the most experienced tabletop facilitator in the world.
Take a look at the video on the right to see what exactly our Cyber Crisis Tabletop Exercises can do for your business.
- Help you achieve compliance and demonstrate commitment to your cybersecurity posture.
- Build muscle memory for your key Incident Response Team members.
- Allow decision-making practice in a dynamic and highly evolved simulated attack scenario.
Cyber Security Tabletop Exercise Scenarios
Here's a glimpse of some of the Cyber Tabletop Exercise Scenario Examples that the session may be based on. These are generic scenarios that are then finetuned to your business context and organisational risks.
We pride ourselves on providing an exceptional service to our clients, but you don’t just have to take our word for it. Read what our clients have to say about working with us.
"The overall objective was to demonstrate & raise awareness amongst the board members. It is a regulatory obligation to ensure that the board are aware of their duties when it comes to incident response & cyber management. It was very important to run this workshop in my opinion… because although we have incident response plans internally, it was imperative to test them & the board’s engagement with a well-defined scenario created by myself and Amar.
The muscle memory for the board and raising awareness among them regarding roles and responsibilities were the key tangible benefits. We’ve also been able to test the board’s decision-making skills which was vital. Improved awareness amongst board members regarding Cyber Incident Response and other Cybersecurity issues was evident, especially after the second workshop. For many organisations, I would recommend that it should be on their agenda to run a workshop like this, especially from a board perspective."
CIO - Waverton Investment Management
"The facilitator conducted the fact finding and then planned the ransomware scenario to make it relevant and contextual to our organisation. Further, the exercise was conducted in a way that made the scenario feel real for the participants. They were encouraged to think like and respond as they would in an actual crisis.
Amar is a great facilitator. He is highly experienced which makes his insights very useful to all participants. But more importantly, he really knows how to engage a room full of business executives who may not always be in the loop with all technical aspects of cyber and ransomware prevention and response.
The ransomware tabletop exercise conducted by Cyber Management Alliance gave us exactly the kind of output we were expecting and met all our objectives.
The executive report shared with us at the end was insightful and highlighted our strengths and weaknesses clearly. We know what needs to be worked upon and where we need more clarity. Thanks CM-Alliance and Amar for this extremely helpful and critical exercise in our overall cyber resilience strategy."
Head of IT Operations, Directorate of Digital Services - Northern Lincolnshire And Goole NHS Foundation Trust
"We selected Cyber Management Alliance to conduct a non-technical, scenario-based, cyber-attack table-top exercise for members of our senior management. Amar Singh is an excellent facilitator and is highly experienced which makes his insights useful to all participants. He engaged our incident response handling team and presented highly technical concepts in a non-technical, easy to understand manner.
The session and scenarios were relevant to our business and the tabletop ransomware exercise was conducted in a deeply engaging and conducive manner and the session met our objectives.”
Chief Finance Officer - Ashling Partners
"We needed something that’s more like a true demonstration of the capability of the business to actually respond. I wanted to get a fresh approach and that's why we opted for CM-Alliance’s CCTE Assessment.
Amar and I spent a good amount of time talking through options and planning the right scenario(s) for the tabletop test; We tried our best to design the scenarios to be challenging enough and both engaging and exciting to be a part of. The CCTE & the corresponding audit conducted has given us insights to reinforce our cyber strategy by continuing to help build the picture of where we were, where we are now and our next focussed steps. We will be engaging CM-Alliance on an annual basis.”
Strategic Technology Leader - Aster Group, UK
"The sessions and scenarios were relevant to our business and the tabletop ransomware exercises were conducted in a deeply engaging manner. The ransomware communication response templates were comprehensive and completely relevant to our business context and the accompanying communication plan was fit-for-purpose. Amar Singh is an excellent facilitator and is highly experienced which makes his insights useful to all participants. Importantly, Amar knows how to engage a room full of business executives and is able to present highly technical concepts in a nontechnical, easy to understand manner.”
Head of Global Security, Risk and IT Compliance - SIG Global
"Cyber Management Alliance Ltd assigned their top and experienced security consultants to deliver our requirements. The consultants worked closely with my team and conducted output focused workshops to then plan, produce and conduct deeply engaging tabletop exercises.
CM-Alliance’s methodology and approach helped extract the most relevant information and data to enable them to construct highly relevant attack scenarios.
Both the technical and executive tabletop sessions conducted by Cyber Management Alliance Ltd met all our objectives. The attendees from both the sessions were impressed with the facilitation and the outcome-driven approach and left the participants more informed and aware of the response processes and procedures.”
IT Compliance Manager - Otsuka Pharmaceutical Europe Ltd
The Management Report/Executive Summary
In the report, we start with an executive brief, present the summary and detailed findings and provide recommendations on all 10 attributes we measure during
the workshop.
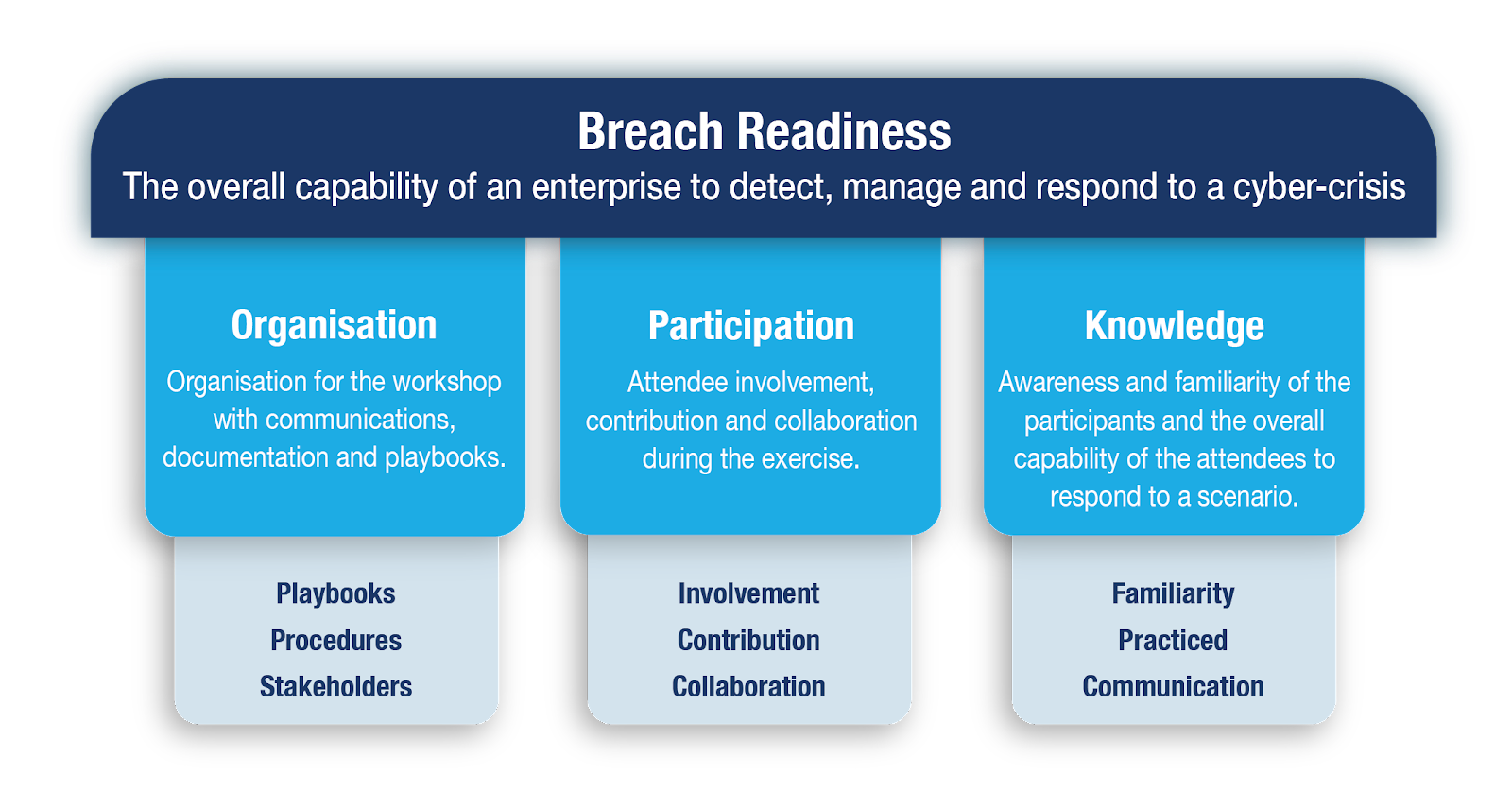
Maturity Scoring Categories
We take a formal, structured approach to our assessment and assess the tabletop exercise against three categories, namely, Organisation, Participation and Knowledge. These domains provide an indication about your organisation’s Breach Readiness; your overall capability to detect, manage and respond to a cyber-crisis. Each category is further broken down into subcategories. The diagram on the right lists each subcategory. Furthermore, each subcategory is marked against a maturity of 1 – 5.
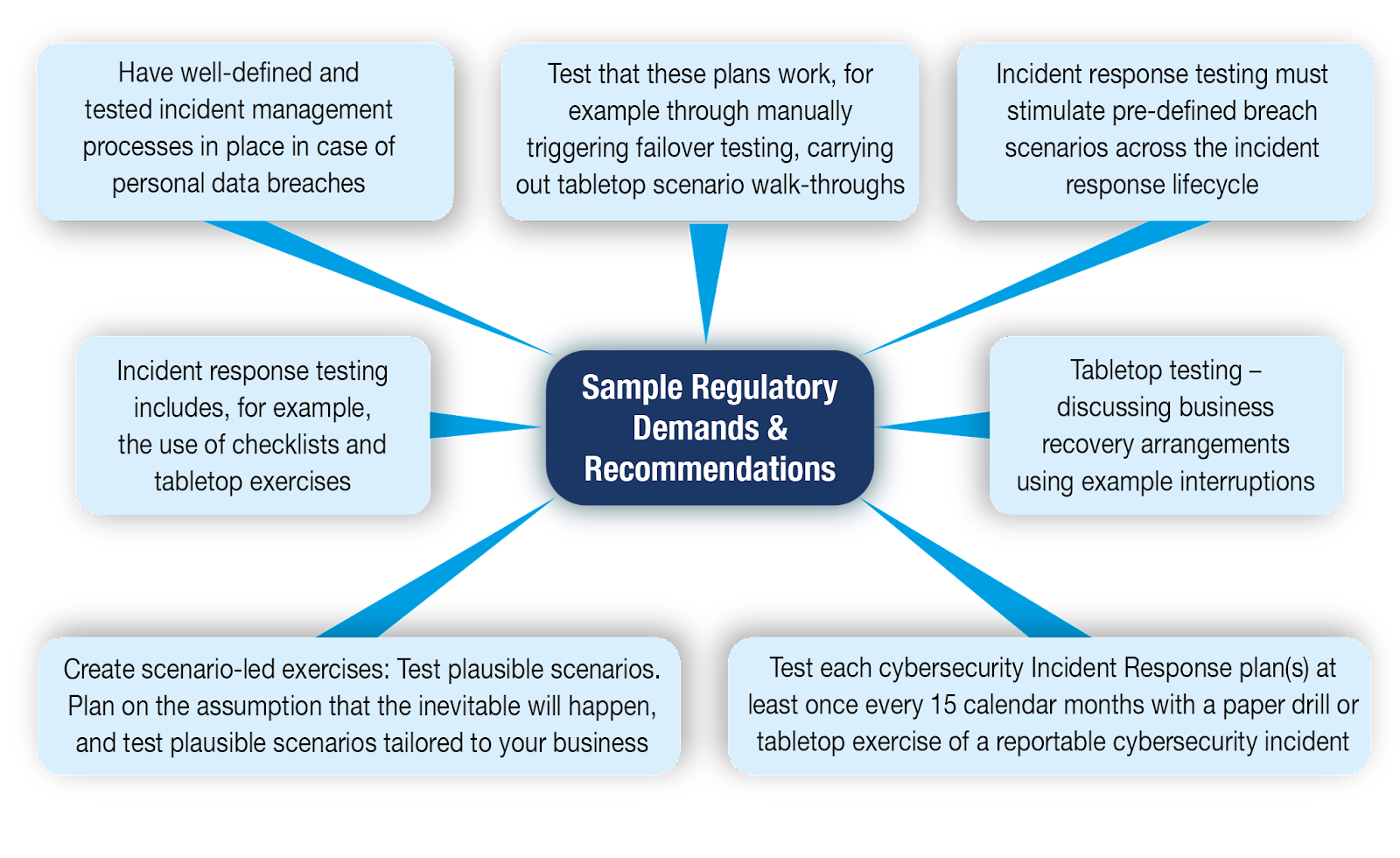
Regulatory Drivers for Cyber Attack Simulation Exercises
Nations and regulatory bodies across the world are introducing specific requirements asking organisations to carry out frequent, structured and scenario-based cyber-attack tabletop exercises to:
- Demonstrate their breach-readiness and organisational capability in cyber incident & crisis management.
- Help organisations be better prepared and equipped to manage the different aspects of a cyber-crisis.
These compliance requirements and guidelines are generally specific to entities operating in the banking, finance, insurance, critical national infrastructure and the government sectors. However, It can be a challenge to meet these compliance requirements and design a plan of action that can help an organisation achieve these regulatory demands. CM-Alliance has designed the Cyber Crisis Tabletop Exercise to help businesses achieve their annual compliance requirements and prepare management and executives to be ready for an actual crisis.
The Figure below lists some of the regulations and guidance from around the world:
Why Choose Us For Your Cyber Security Drills?
We are one of the world’s leading independent cyber incident & crisis management authority offering advisory services, executive training, and bespoke workshops in all aspects of cyber crisis management, incident planning, incident-response testing and tabletop exercises.
We are the creators of the internationally acclaimed UK-Government’s NCSC Assured Cyber Incident Planning and Response (CIPR) training and have trained attendees from organisations including the United Nations, UK Ministry of Defence, several UK Police Forces, NHS Trusts, European Central Bank, Swiss National Bank, Microsoft, Ernst and Young and many others.
Take a look at some of our Tabletop Exercise Case Studies for a deeper understanding of how we have helped our clients improve their resilience against cyber-attacks.
Trusted by

.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
Executive Briefings and Cyber Crisis Tabletop Exercises
- Annual
- Monthly
- GBP
- USD
- EUR
For the Technical CCTE, we recommend the Client to record the session for audit purposes. Cyber Management Alliance Ltd will only
provide a remote human observer and there will an additional charge.
Recommended Participants & Stakeholders for the Cyber Tabletop Exercise
| Board/Directors and Executive Leadership (CEO, COO, CIO, CISO, IT Director) |
| Head of Information Security, Head of Audit, Head of Compliance |
| Crisis Management Team, Cybersecurity Incident Response Team |
| Crisis Communications Team |
| Legal, Regulatory, Data Privacy, Communications and Public Relations Team, Human Resources Team |
| Business Continuity Managers/Teams |
| Physical Security |
| Product Owners, Product Technical Leads |
| Service Manager/Change Manager |
| IT Security, System and/or Network Administrators |
| Key Developers |
| Database Administrators |
| SoC or Monitoring Team |
| Third-party Equipment Vendors (represented by exercise facilitators) |
| Third-party Cybersecurity Insurance Providers, Forensics / Incident Responders, Ransomware Negotiators and/or PR Agency (represented by exercise facilitators) |
| Regulatory Authorities (simulation through exercise facilitators) |
Why not book a discovery call to discuss your requirements?
Want more information on our Cyber Tabletop Exercises and how we can customise one that's right for you? Book a no-obligation discovery call with one of our consultants.
The information on this page and related pages and documents is Copyright of Cyber Management Alliance Ltd. The VCA or Virtual Cyber Assistant term, other terms, information, concepts, ideas, workflows, processes, procedures and other content that directly or indirectly supports the VCA Service are Copyright of Cyber Management Alliance Ltd. Copyright 2022.



