Why hire a Virtual CISO or vCISO?
The cybersecurity industry is riddled with a shortage of skilled personnel, making it very difficult for organisations to hire effective cybersecurity staff and CISOs. This problem is amplified for start-ups and small-to-medium businesses who often also lack the massive budgets required to hire and retain the right kind of people. Our Virtual CISO services or 'CISO as a Service' can help plug the many gaps that exist in the current landscape. Our Virtual CISO advisors bring rich, cross-industry experience to fulfill your specific organisational needs.
Skills shortage making it very expensive to hire full-time staff
Dearth of personnel with broad knowledge & multi-sector context
Complex advice by most external consultancies, designed to confuse and increase spend
Inflexible & Rigid Approach to Billing & Services + Complicated Tactics to stretch length of contract
Three Key Benefits of our vCISO Service
Cost Effective Professionals (CISO Advisors) at your beck and call
Experienced security consultants at a fraction of the cost!
Professional advice on prioritising technology investments
Our aim is to save our clients' money and we achieve this by offering pragmatic and practical advice. Our Virtual CISO Consulting Services often helps reduce overall investments in unnecessary technology stacks.
Increased engagement with your Board, Senior Executives & Management
True cyber-resiliency starts from the top. We speak the language of business to engage all executives. Our vCISOs are specialists in engaging and presenting to a range of senior executives, board members & non-technical senior staff. With our Virtual CISO Advisory services you can be assured of greater board engagement.
Our Vision & Mission Behind the vCISO Service
CM-Alliance’s primary objective with the Virtual CISO Advisory Services is to make our clients fully cyber-resilient and to enable them to protect against known threats. We also aim to assist them in rapidly detecting, responding to and recovering from advanced cyber-attacks so they can conduct their business uninterrupted.
How do we achieve this mission??
We do this by Identifying organisational risks and threats; creating, improving and assisting to deploy technology controls, processes and policies to Protect the organisation from cyber-attacks and helping make the organisation beach-ready so it can rapidly Detect, Respond to and Recover from a cyber-attack.
Our Standards-Based Approach:
At Cyber Management Alliance, we take co-ownership of your challenges and risks and aim to improve your organisation’s Cybersecurity and Cyber resilience posture through our professional services and experienced staff.
Flexibility
Average cost savings. No, really!
Savings on training & termination costs.
Headache & Wait time.
The 15 Service Domains of our Virtual CISO Consulting Services?
We cover 15 main service domains in our Virtual CISO UK programme. There are several sub-categories under each domain. Get in touch with us for a more detailed understanding of the 250 service categories our Virtual CISO advisors can help you with.
Activities & Tasks Undertaken by Our vCISOs
For our Virtual CISO Consulting Services, we have divided client requirements into three clearly defined tasks or activities:
• Review + Comment: We will review your artefacts (cybersecurity documents, policies etc.) & provide our professional opinions.
• Review + Refresh: We will review existing artefacts, understand your processes & where required refresh the documents to align with best practices.
• Create: We will understand the organisational context, the business processes and create relevant artefacts based on best practices and applicability to the organisation.
6 Reasons Why Our Clients Opt for our vCISO Service
There is a reason clients in UK, Oman, Singapore, Scotland, Dubai, Switzerland, Saudi Arabia, US and elsewhere trust Cyber Management Alliance.
We set the highest bar for cost effective, top quality vCISO services.
Get in touch if you want us to create, review or refresh your policies, processes and procedures or if you want to ensure you comply with ISO 27001:2013 or Cyber Essentials or NIST's Cybersecurity Framework.
Trusted & Impartial
We offer trusted impartial guidance, advice and professional support from globally-recognised experienced professionals.
Long-term Partner
Organisations are in long-term partnerships with Cyber Management Alliance Ltd and treat us an extension of their business.
Strong People Skills
Humans are complex beings and we fully understand and respect office politics and human dynamics and navigate these effortlessly.
Vendor-neutral Context & Guidance
Although we know the cybersecurity market really well, our vCISO service does not sell any products or solutions. We don't endorse any vendor or brand.
Top-notch Cyber Professionals
We offer you access to a world class 'CISO as a service' (Virtual CISO Advisory Services), underpinned by our carefully-recruited cybersecurity consultants.
Top Quality at Great Value
The USP of our vCISO service is its cost-effectiveness. We are able to compete with global providers whilst maintaining 100% of our recognised quality service.
Trusted by

.png?width=800&height=362&name=FIFA_series_logo.svg%20(1).png)



.svg.png?width=1200&height=389&name=1200px-Capita_logo_(2019).svg.png)
More reasons to hire our vCISOs...
There are literally over a hundred reasons why most organisations should hire our vCISOs.
You must be wondering, why bother with a hiring an external consultant (we prefer to use the word vCISO or virtual Cyber Information Security Officer) for your business. Surely, you can hire a full time staff or do it yourself? So, here's a quick snapshot of the key reasons why our clients hire our vCISOs:
- Access to a pool of experienced CISOs (you're lucky if you can get even one good full time CISO).
- Our CISOs know how to engage all kinds of stakeholders.
- Our CISOs have the battles-scars and hit the ground running almost immediately.
- Our vCISOs have exceptional leadership and skills to help define, plan and execute bespoke strategies unique to your organisation.
- Our vCISOs are supported by a whole backend team of consultants, risk, compliance and governance teams to ensure we meet all the varying requirements of your business.
You can download our special vCISO v Full Time CISO PDF here.

Client Feedback
Listen to what our clients have to say about our vCISO service
"In order for BMJ to the right way forward we looked for a VCISO to advise us on the right way to do things and give us expertise. We went to Cyber Management Alliance and it's been about a year now and we ran workshops, looked at our response to incidents, created the incident response plan and we are in a position now where we understand our way forward. Our VCISO keeps us on our toes and overall it's been a very effective way of delivering expertise into the organisation that we wouldn't have normally had."
Aaron Townsend, Service Delivery Manager, British Medical Journal
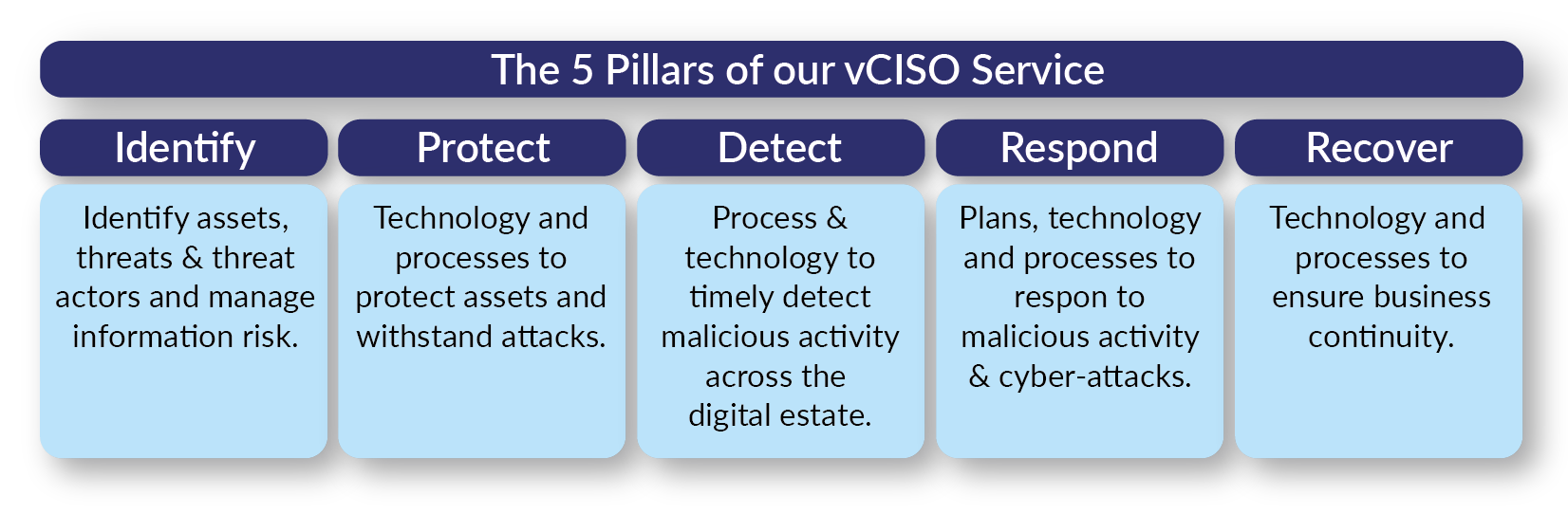
5 Pillars of our vCISO Services
Our vCISO service is based on five key pillars - Identify, Protect, Detect, Respond & Recover
The table on the left summarises each category.
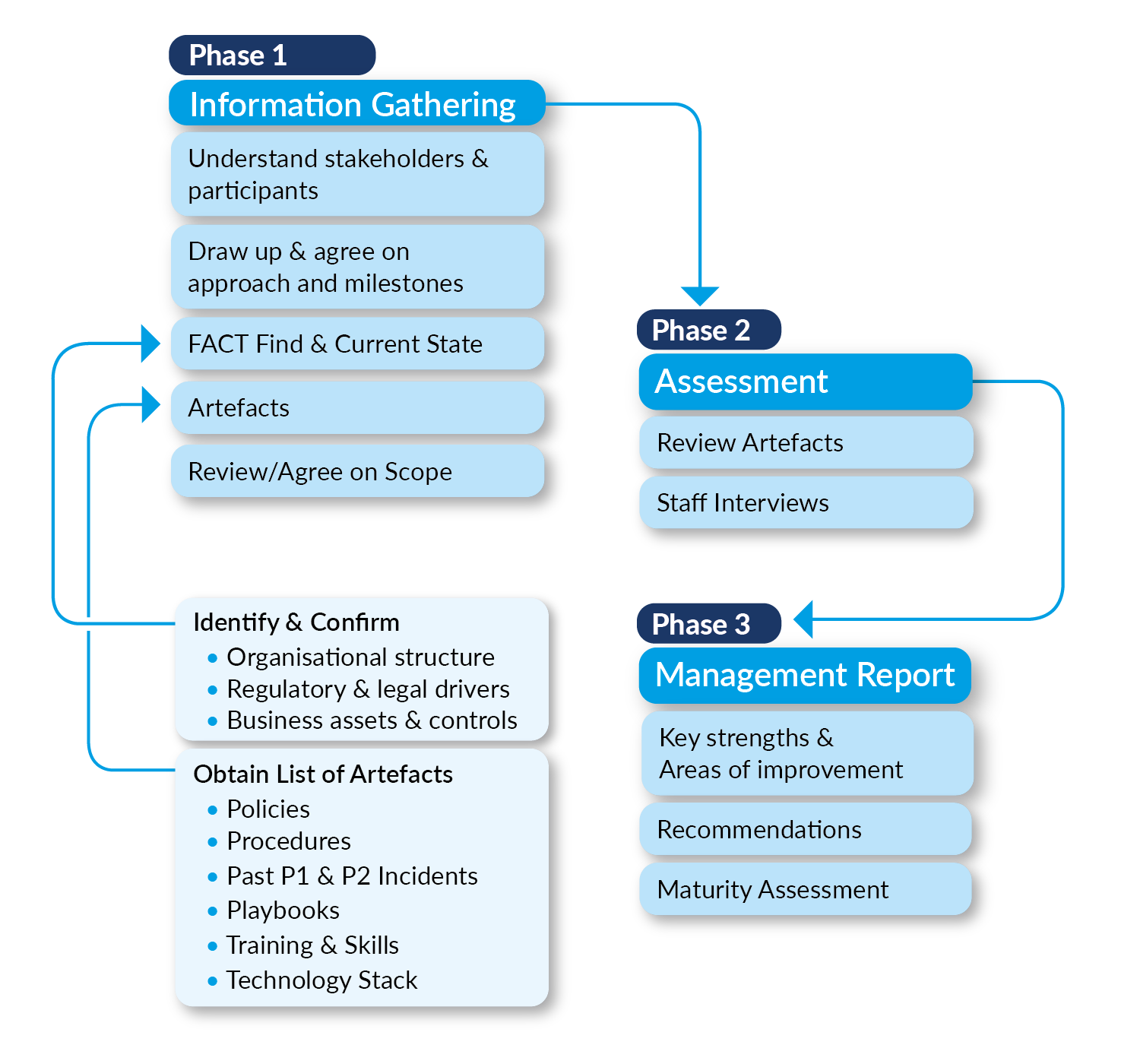
The VCISO Process Workflow
As soon as a client signs us on, we conduct a NIST-Based Cyber Health Check & overall Assessment of artefacts before agreeing on the next set of important activities and selecting one or more service domains. The workflow includes the following:
- A review of the artefacts & agreeing on the scope.
- An assessment of the artefacts & staff interviews.
- A management report detailing recommendations and areas of improvement.
What does a virtual CISO do?
A small snapshot of the Virtual CISO Job Description & the V CISO roles and responsibilities...
Complete Assistance on Artefacts
Our expert vCISOs will help you review, refresh & create cybersecurity artefacts including policies & processes. They will also help you align the organisation & related artefacts against a selected standard.
Guidance on Data-Breach Readiness
Our vCISOs oversee and co-ordinate to ensure your business is prepared to deal with data breaches and cyber incidents. They can also assess your breach readiness and advise you on effective strategies for cyber incident response. In a nutshell, they will catalyze your organisation's internal capability in Cybersecurity, Cyber Resilience & Incident Response.
Regulatory Compliance and Governance
Our vCISOs will help you prepare for specific audits and assessments. They will also get you certification-ready in ISO 27001:2013, BCP 22301, UK’s Cyber Essentials, PCI-DSS and others. Apart from this, they will manage and communicate with regulators for all data privacy and information security requests on your behalf.
All trademarks, service marks, trade names, product names, service names and logos appearing on the site, or on printed or digital material are the property of their respective owners, including in Cyber Management Alliance Ltd. Any rights not expressly granted herein are reserved.
What exactly do you get with our Virtual CISO Consulting Services?
Here's a quick look at 10 of the main service domains that we cover in our Virtual CISO UK programme. There are several sub-categories under each domain, some of which have been listed below.
Cybersecurity & Cyber Resilience
1. Cybersecurity Strategy
2. Cybersecurity Policy & Procedures
3. Cybersecurity Roles & Responsibilities
4. Crisis Management Procedures
5. Disaster Recover & Business Continuity Plans
Incident Response & Incident Management
1. Incident Response Plan
2. Policies, Plans & Procedures
3. Playbooks
4. Threat Actor Library
5. Mapping of incidents/Security events
Risk Assessment & Risk Management
1. Risk assessment
2. Risk mitigation plan/Risk prioritization
3. Audit/Assessment reports
4. Incident tracker & Change management tracker - Major Changes
5. Information asset registers
Supply Chain
1. Agreements with Suppliers
2. Requirements in Supply chain
3. Evaluation of cybersecurity controls in supply chain
4. Policies & Procedures
5. Evaluation & Monitoring checklists
Certifications
1. Gap assessment
2. Measurement effectiveness of controls
3. Previous audit report closures
4. Implementation of controls
5. ISO 27001 & Cyber Essentials
Governance & Compliance
1. Policies & Procedures
2. Measurement effectiveness
3. Compliance to organisational framework
4. Audit plans & Assessment reports
5. Information security strategy
Technology Deployment
1. Architecture diagram
2. Comparison of solutions
3. Configuration
4. Monitoring
Data Security
1. Information classification
2. Data flow analysis
3. Information access controls/restrictions
4. Data leakage controls
Operations Security
1. Policies
2. IT Procedures
3. Configuration guidelines
4. Incident/Problem Management
5. Effectiveness of IT Security controls
Asset Management
1. Asset Management
2. Information asset registers
3. Information classification and labelling
4. Asset criticality
5. Asset handling procedures

